How to Share Google Sheets Call Logs Securely Across Teams
-
Bella Williams
- 10 min read
Secure Call Log Sharing with Google Sheets emphasizes the importance of data security in collaborative environments. In today's dynamic work environments, sharing call logs securely across teams is crucial for maintaining trust and confidentiality. Google Sheets offers an accessible platform for this task, but it requires proper protocols to ensure sensitive information remains protected.
When teams utilize Google Sheets for call logs, comprehending security measures becomes paramount. This guide will delve into the steps necessary for effective secure call log sharing, addressing potential vulnerabilities while ensuring seamless accessibility for authorized users. By understanding the mechanisms behind secure data sharing, teams can improve collaboration without compromising privacy.
Analyze & Evaluate Calls. At Scale.
Understanding Google Sheets Capabilities for Secure Call Log Sharing
Google Sheets serves as an excellent platform for secure call log sharing among teams, offering functionality that balances accessibility with privacy. One of the standout capabilities is its robust permission settings, enabling users to determine who can view or edit the call logs. This feature is essential for maintaining data confidentiality while promoting collaboration among team members.
Another significant capability of Google Sheets is its real-time data updating. Changes made by one user are instantly visible to others, ensuring that all team members have access to the latest information. Additionally, Google Sheets automatically saves revisions, allowing teams to track alterations and revert to previous versions if necessary, enhancing the security of the shared data. These combined features make Google Sheets a powerful tool for secure call log sharing, ultimately improving team efficiency and accountability while safeguarding sensitive information.
Benefits of Using Google Sheets
Google Sheets offers a seamless platform for secure call log sharing among teams, enhancing collaboration and data management. One primary benefit lies in its real-time editing capabilities, allowing multiple users to access and edit logs simultaneously. This ensures that team members always have the most up-to-date information at their fingertips, fostering efficiency in workflows.
Another significant advantage is the ability to set granular permissions for users. This feature enables teams to control who can view or edit specific call log entries, adding a layer of security to the data. In addition, Google Sheets integrates smoothly with various tools, which can automate processes and improve productivity. By embracing these features, teams can ensure secure call log sharing while maintaining data integrity and accessibility. Overall, utilizing Google Sheets maximizes both collaboration and security in managing call logs.
Potential Security Risks and How to Mitigate Them
Sharing call logs via Google Sheets can pose several security risks, requiring vigilance and proactive measures to safeguard sensitive information. One primary risk involves unauthorized access to the logs, which may contain personal or confidential details. To mitigate this, setting strict permissions for who can view or edit the document is crucial. Regular reviews of access settings can also further enhance security, ensuring that only those who need to see the data have the ability to do so.
Another significant concern is data breaches due to phishing or malware attacks. Employing encryption can help protect the logs during transmission and storage. Additionally, implementing two-factor authentication adds an extra layer of security, making unauthorized access more difficult. By being aware of these risks and actively managing them, teams can achieve secure call log sharing while ensuring compliance with data privacy regulations.
Steps to Ensure Secure Call Log Sharing
To ensure secure call log sharing, start by setting proper permissions and access controls. Begin by identifying team members who require access to the Google Sheets call logs. Assign varying permissions based on individual roles, ensuring that only authorized personnel can edit or view sensitive data. This step is crucial for maintaining data integrity and confidentiality within your organization.
Next, utilize encryption to enhance security further. Encryption protects your data both at rest and in transit, shielding it from unauthorized access during transmission. Implement strong passwords and consider multi-factor authentication to add another layer of protection. Finally, don’t overlook the importance of conducting regular audits and monitoring activities in your shared Google Sheets. This practice helps identify unusual access patterns or potential breaches, allowing for swift action. By following these steps, your teams can share call logs securely while minimizing risks.
Step 1: Setting Up Permissions and Access Controls
To ensure secure call log sharing across teams using Google Sheets, setting up permissions and access controls is essential. Begin by identifying the team members who need access to the call logs. This step not only determines who can view or edit the data but also helps in minimizing the risk of unauthorized access. Carefully consider the level of access each member requires. For instance, some may need only view permissions, while others might require edit capabilities.
Once you've identified the necessary permissions, navigate to the Google Sheets sharing settings. Adjust permissions to reflect the access levels you've identified. It is crucial to regularly review these permissions as team dynamics change. Establishing these controls lays the foundation for secure call log sharing, protecting sensitive information and ensuring that only authorized personnel can interact with the data. Taking these proactive steps significantly enhances the overall security of your shared call logs.
Step 2: Using Encryption for Enhanced Security
To ensure Secure Call Log Sharing, encryption is a vital step in enriching security protocols. Encrypting your Google Sheets with call logs allows you to protect sensitive information from unauthorized access. By applying encryption, only individuals with the correct decryption key can view the content, safeguarding it against potential breaches.
There are several methods to implement encryption effectively. First, use Google’s built-in encryption options, which automatically secures data when it is stored and transferred. Secondly, consider employing third-party encryption tools that provide additional layers of security. These tools can encrypt files before uploading them to Google Drive, ensuring that your call logs remain confidential. Lastly, regularly update your encryption methods to keep up with current security standards, thereby reinforcing your defense against emerging threats. By incorporating these practices, you can maintain a secure environment for your team’s communication and data sharing.
Step 3: Implementing Regular Audits and Monitoring
In Step 3: Implementing Regular Audits and Monitoring, ongoing oversight becomes essential to maintaining secure call log sharing. Regular audits help identify potential security breaches, ensuring that sensitive information remains protected. Monitoring call log access and changes will provide insights into user behavior, helping teams to quickly address any anomalies that may arise.
To effectively implement regular audits, establish a schedule for reviewing access logs and permissions. Start by evaluating who has access to call logs and ensure that permissions are appropriate. Next, implement automated alerts for unauthorized access attempts or unusual activities. Finally, document findings and adjustments, as this creates a transparent overview of security practices. By actively engaging in audits and monitoring, teams can foster a culture of accountability and ensure that secure call log sharing principles are consistently upheld.
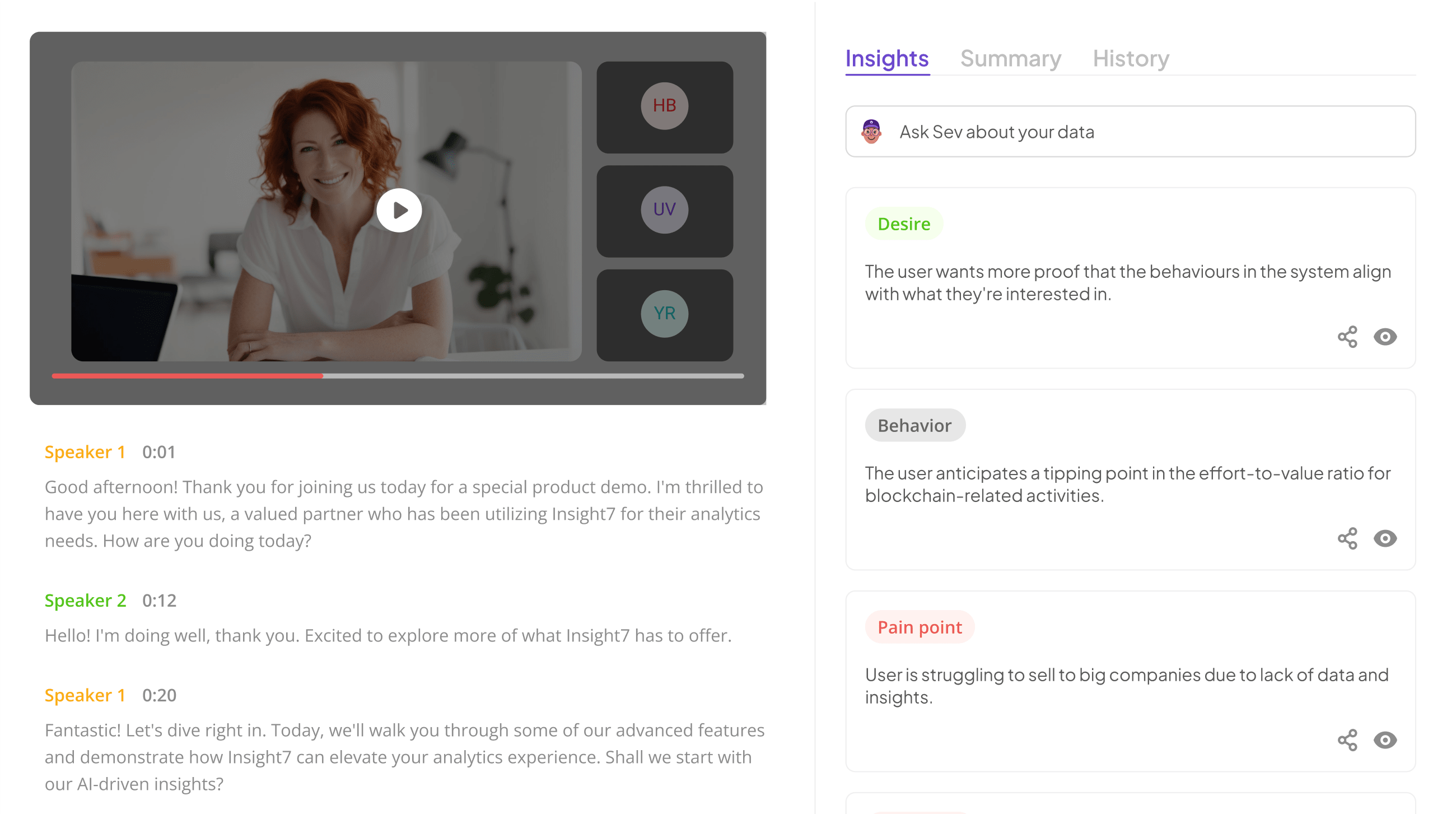
Extract insights from interviews, calls, surveys and reviews for insights in minutes
Tools to Support Secure Call Log Sharing
To support secure call log sharing, various tools can be employed to enhance collaboration across teams. Insight7 is instrumental for quantitative analysis and provides valuable insights when evaluating call log data. It helps streamline reporting and ensures that data is reliable and actionable. Utilizing automated workflows designed through Zapier can also facilitate data flow between multiple platforms without compromising security.
Google Workspace offers robust security features, which include two-factor authentication and advanced sharing permissions. These existing features can significantly reduce unauthorized access to sensitive information. Trello serves as an effective platform for team coordination; it allows members to track tasks related to call logs securely. LastPass is another essential tool for managing passwords and access, ensuring that only authorized team members can view and edit call logs.
Incorporating these tools will engage teams effectively while prioritizing secure call log sharing. By leveraging the right resources, organizations can maintain the trust of their stakeholders and protect valuable communication data.
insight7
For effective and secure call log sharing across teams, it's essential to grasp the nuances of Google Sheets. Utilizing Google Sheets provides an organized, easily accessible platform for your call logs. However, sharing sensitive information securely requires attention to detail. Begin by ensuring that only authorized personnel have access to the sheet. This initial step can drastically reduce the risk of unauthorized viewings and potential data breaches.
Next, consider integrating encryptions into your workflow. While Google Sheets offers basic security measures, additional encryption can provide a second layer of protection. Regular audits and monitoring of access should also be implemented to track who is viewing or editing the logs. These practices create a resilient system for secure call log sharing, fostering trust among team members and safeguarding sensitive information. By prioritizing these methods, your team can collaborate effectively without compromising security.
Google Workspace Security Features
Google Workspace provides robust security features that are vital for ensuring secure call log sharing between teams. These tools help protect sensitive data while facilitating collaboration. Key elements include user authentication, access restrictions, and real-time monitoring. Leveraging these features minimizes the risk of unauthorized access and ensures compliance with data protection policies.
One of the standout security features is the ability to set granular permissions. This means you can control who can view or edit call logs in Google Sheets. Additionally, multi-factor authentication adds an extra layer of security, making it more challenging for cyber threats to compromise accounts. Regular auditing and activity tracking allow teams to identify potential security breaches promptly. By understanding and utilizing these features, organizations can ensure that sharing call logs is not just effective, but secure.
Zapier for Automated Workflows
Automating workflows with Zapier can significantly enhance the efficiency of sharing call logs securely across teams. By integrating Zapier with Google Sheets, you can create automated triggers that instantly upload call log data, ensuring that your team stays informed without manual intervention. This seamless connection minimizes the risk of data entry errors and helps maintain the integrity of your call logs.
To set up secure call log sharing, you can take the following steps. First, create a Zap that triggers whenever new call log data is entered. Next, configure actions to automatically send notifications to team members or update relevant channels in apps like Slack or Trello. Lastly, ensure that each integration follows the necessary security measures to protect sensitive data. This way, you’ll streamline operations while safeguarding your information from unauthorized access, making collaboration smooth and secure.
Trello for Team Coordination and Monitoring
Effective team coordination is essential for successful secure call log sharing. Trello serves as an invaluable tool for this purpose, enabling seamless collaboration, task management, and monitoring among teams. By organizing tasks into boards, lists, and cards, team members can track the progress of call logs, ensuring that everyone is on the same page regarding updates and responsibilities.
Utilizing Trello promotes transparency and accountability within the team. Each member can easily access shared call logs, view deadlines, and assign tasks related to data analysis or follow-ups. Integrating Trello with Google Sheets enhances efficiency, allowing real-time updates to information and facilitating swift decisions. As teams streamline their processes with Trello, they not only improve coordination but also prioritize secure call log sharing—essential for maintaining confidentiality and trust in collaborative efforts. This approach creates a structured, clear path for managing information and supporting team goals effectively.
LastPass for Secure Access Management
Effective management of access credentials is essential when sharing Google Sheets call logs securely across teams. LastPass provides a user-friendly solution designed to enhance security through secure access management. By using LastPass to store and share passwords, team members can easily log into shared resources without the risk of exposing sensitive information.
Implementing LastPass simplifies the process of secure call log sharing by offering features such as password vaults, two-factor authentication, and encrypted sharing. First, team members can create unique passwords for each shared resource, ensuring that access remains restricted. Next, utilizing LastPass’s sharing capabilities means you can grant or revoke access to call logs dynamically, offering flexibility to manage team collaborations effectively. Ultimately, investing in tools like LastPass not only fosters a culture of security but also streamlines the process of sharing sensitive call logs securely across teams.
Conclusion: Best Practices for Secure Call Log Sharing
When considering best practices for secure call log sharing, it’s essential to prioritize both data integrity and accessibility. Establishing clear protocols for access controls ensures only authorized team members can view sensitive information. Regular audits help maintain awareness of who has access to the logs, preventing unintended breaches. Encryption further safeguards data during transmission, keeping confidential details secure.
Teams should also leverage technology, such as Google Sheets, to facilitate seamless collaboration while implementing security features. Creating a culture of responsibility around data sharing empowers all team members to prioritize secure call log sharing. By combining awareness, technology, and compliance, organizations can effectively protect valuable call data while enhancing teamwork.