The Most Secure QA Software for Regulated Industries (SOC2, HIPAA, GDPR)
-
Bella Williams
- 10 min read
Regulated QA Security is essential for software development, particularly in industries governed by strict compliance standards. As organizations strive to ensure data integrity and privacy, the need for secure quality assurance practices becomes paramount. These protocols not only protect sensitive information but also foster trust among users and stakeholders.
In an environment where regulations shape operational procedures, organizations must adopt robust quality assurance methodologies. This introduction provides insight into the importance of implementing effective QA security measures tailored for compliance with industry regulations. Understanding these requirements will enable businesses to navigate the complexities of regulated environments effectively while safeguarding their data and reputation.
Analyze & Evaluate Calls. At Scale.
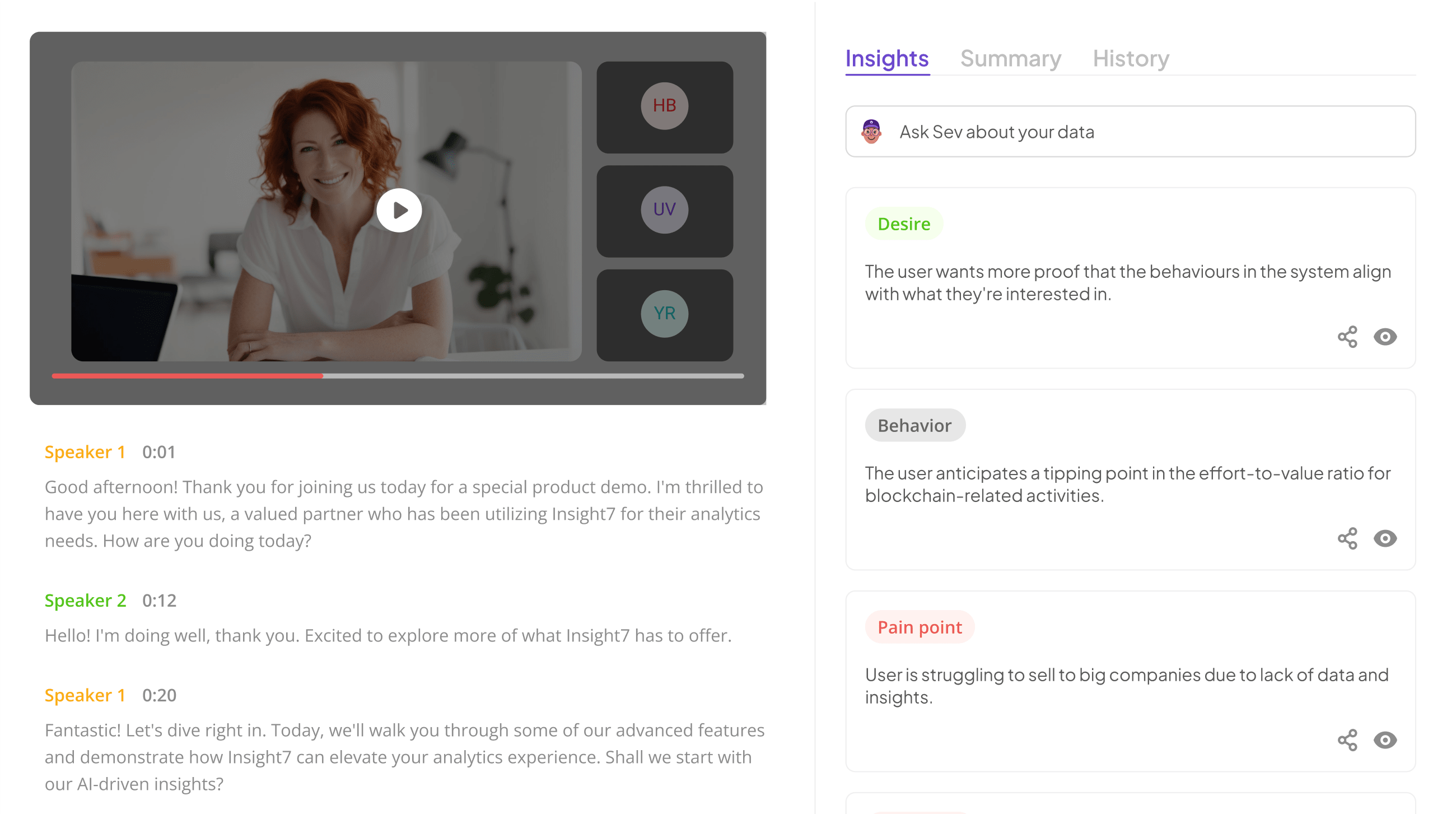
Key Features of Regulated QA Security Software
Regulated QA security software is designed to meet the stringent demands of industries governed by compliance standards such as SOC2, HIPAA, and GDPR. One of the core features is robust risk management, ensuring that potential vulnerabilities are systematically identified and mitigated throughout the software development lifecycle. Automation in quality assurance processes also enhances security, allowing teams to conduct frequent tests without compromising on thoroughness.
Another essential characteristic is comprehensive auditing capabilities. This feature enables organizations to maintain detailed records of compliance and performance evaluations, which are crucial for addressing regulatory requirements. Additionally, data encryption is critical, safeguarding sensitive information both at rest and during transmission, thereby minimizing the risk of data breaches. Overall, the integration of these key features not only strengthens security but also fosters a culture of accountability and transparency in regulated environments.
Compliance-Driven Security Protocols
Compliance-driven security protocols are foundational to maintaining the integrity and security of sensitive data across regulated industries. These protocols serve as a framework that guides organizations in implementing measures necessary for data protection and risk management. The complexities of compliance with standards such as SOC2, HIPAA, and GDPR underscore the necessity of adopting robust security frameworks that prioritize confidentiality and integrity.
To effectively navigate these compliance requirements, organizations must adopt key protocols. Firstly, access controls should be implemented to ensure only authorized personnel can view sensitive information. Secondly, regular audits and assessments are essential for identifying vulnerabilities and ensuring adherence to compliance standards. Lastly, data encryption must be utilized during transmission and storage to protect against unauthorized access. By prioritizing these compliance-driven security protocols, organizations can better safeguard their data assets, ensuring both regulatory compliance and customer trust in their services.
Ensuring Data Protection and Privacy
Data protection and privacy are paramount in regulated industries, including those adhering to SOC2, HIPAA, and GDPR standards. Ensuring data integrity and confidentiality requires robust security mechanisms within QA processes. The first step involves implementing compliance-driven security protocols that address specific regulations and security needs. This not only protects sensitive information but also fosters trust with clients and stakeholders.
Moreover, organizations must integrate continuous monitoring to detect unauthorized access and data breaches promptly. This proactive approach ensures that any anomalies are swiftly identified, allowing for corrective action. Training employees on cybersecurity awareness is equally vital, as human error remains a significant vulnerability. By establishing these foundational practices, businesses can effectively navigate the complexities of regulated QA security, ensuring the privacy and protection of all data handled within their systems.
Extract insights from interviews, calls, surveys and reviews for insights in minutes
Top Secure QA Software for Regulated Industries
In the realm of regulated QA security, organizations must navigate a complex landscape of compliance and data protection. The demand for robust QA software designed for industries governed by SOC2, HIPAA, and GDPR has risen significantly. These tools aim to ensure that quality assurance processes not only meet but also exceed regulatory standards, providing a secure framework for evaluation and analysis.
When selecting the top secure QA software, it’s essential to consider a few key features. First, compliance-driven security protocols ensure that all operations adhere to industry regulations, enabling organizations to demonstrate accountability. Next, ensuring data protection and privacy is paramount, as these solutions safeguard sensitive information. By integrating these principles, organizations can confidently pursue their quality assurance objectives, knowing they are equipped with top-tier solutions that prioritize regulated QA security and compliance.
insight7: Leading the Charge in QA Security
In the realm of regulated QA security, organizations face unique challenges driven by stringent compliance requirements. To lead the charge in QA security, companies must adopt a robust framework that safeguards sensitive data while ensuring alignment with regulations such as SOC2, HIPAA, and GDPR. This involves implementing advanced security protocols that actively protect against vulnerabilities and unauthorized access.
Effective QA security also prioritizes auditing and monitoring processes. Organizations should conduct regular assessments to identify potential risks and ensure continuous compliance. By fostering a culture of security throughout the software development lifecycle, businesses can not only protect their data but also instill trust in their clients. As technology evolves, staying proactive in quality assurance practices will be vital for meeting regulatory standards and maintaining a competitive edge in regulated industries.
Additional Tools to Consider
To enhance effective Regulated QA Security, it's essential to explore various additional tools that can fortify your security posture. Each tool offers unique capabilities to address specific compliance needs and strengthen your overall quality assurance strategy. By integrating these tools, organizations can not only ensure compliance with regulations like SOC2, HIPAA, and GDPR but also enhance the overall security framework.
Veracode: A leading application security platform that focuses on identifying and mitigating vulnerabilities in software applications through continuous monitoring and assessment. This tool helps ensure that applications remain secure throughout their lifecycle, aligning with regulatory standards.
Checkmarx: This platform specializes in static application security testing, enabling developers to find vulnerabilities early in the development process. By embedding security testing into the continuous integration pipeline, it supports proactive compliance with various industry regulations.
Micro Focus Fortify: A comprehensive solution for scanning applications, it offers dynamic and static analysis capabilities to uncover vulnerabilities during both pre and post-release phases. Its robust reporting features help organizations demonstrate compliance effectively.
IBM AppScan: Renowned for its dynamic testing capabilities, AppScan simulates attacks on applications to identify security weaknesses. It assists organizations in ensuring that applications are secure before they go live, mitigating risks associated with regulatory compliance.
Incorporating these tools will provide significant benefits, including risk reduction and improved security. Together, they help foster an environment where regulated QA security is prioritized, ultimately leading to better compliance outcomes.
Veracode
In the realm of regulated QA security, ensuring the integrity of applications is paramount. A reputable security tool offers vital solutions for organizations managing compliance with frameworks like SOC2, HIPAA, and GDPR. It proactively identifies vulnerabilities in code, allowing teams to address potential risks before deployment. With the increasing incidence of data breaches, having robust security measures becomes essential for maintaining trust and compliance within regulated industries.
Furthermore, incorporating thorough testing practices enhances software reliability. Automated scanning tools streamline the process, enabling quick assessments without disrupting development schedules. Regular monitoring not only fortifies the security posture but also cultivates an organizational culture of proactive risk management. By doing so, businesses can confidently comply with evolving regulations while delivering secure software solutions to their customers. Integrating a solution dedicated to regulated QA security is no longer a choice; it’s a necessity to thrive in today’s digital landscape.
Checkmarx
In the realm of regulated QA security, a tool stands out for its unique capabilities in identifying and mitigating vulnerabilities in code. Its extensive scanning features help organizations enhance their software security posture, particularly in sectors governed by strict compliance standards like SOC2, HIPAA, and GDPR. Through automated checks and detailed reports, this solution allows development teams to address security concerns before they become critical issues, ultimately fostering safer applications.
Understanding the tool's importance within regulated industries, it integrates seamlessly into development workflows. The sophisticated analysis it provides empowers teams to make informed decisions, ensuring that security is maintained throughout the software development lifecycle. This proactive approach to security not only enhances compliance but also builds trust with clients and stakeholders, solidifying a firm's reputation in a competitive landscape. By prioritizing regulated QA security, organizations can navigate the complexities of compliance with greater assurance and efficiency.
Micro Focus Fortify
Micro Focus Fortify stands out as a crucial tool for ensuring regulated QA security in software development for industries bound by SOC2, HIPAA, and GDPR. This robust platform provides comprehensive security testing capabilities, designed to identify vulnerabilities in the early stages of the software development lifecycle. By integrating security into the development process, organizations can reduce potential risks while ensuring compliance with stringent regulations.
The platform offers static and dynamic analysis, enabling teams to detect security flaws in both legacy and modern applications. Furthermore, it offers seamless integration with existing development environments, which enhances collaboration among development, security, and operations teams. By prioritizing regulated QA security, organizations can foster trust while protecting sensitive data and adhering to compliance mandates. Investing in this solution not only safeguards the organization but also builds confidence in customer interactions, making it an indispensable asset in today’s regulatory landscape.
IBM AppScan
IBM AppScan is a powerful tool designed specifically for ensuring Regulated QA Security in software development for industries subject to stringent compliance standards. This application helps identify security vulnerabilities early in the development process, enabling organizations to maintain adherence to regulations like SOC2, HIPAA, and GDPR. By scanning both web applications and APIs, it provides detailed reports on potential threats, empowering teams to address problems proactively.
Understanding the complexities of security compliance can be daunting. This solution not only automates testing but also incorporates guidelines aligned with various regulatory frameworks. Its capabilities extend to continuous monitoring, allowing for real-time updates on security postures throughout development. As a result, businesses can confidently deliver secure applications while meeting their compliance obligations. By integrating tools like IBM AppScan into the QA process, organizations can foster a culture of security awareness and protect sensitive data effectively.
Conclusion: Choosing the Best Regulated QA Security for Your Needs
When selecting the most suitable Regulated QA Security for your organization, start by assessing your specific compliance needs. Different industries have unique requirements, such as SOC2, HIPAA, and GDPR. Understanding these regulations will guide you toward software solutions designed to maintain those standards effectively. The right tool will streamline your QA processes while ensuring data protection and privacy.
Moreover, consider user-friendliness, scalability, and integration capabilities of the software. Look for systems that offer customizable templates and evaluation criteria tailored to your industry. By prioritizing these elements, you can safeguard your data while promoting quality assurance. Ultimately, investing in the best Regulated QA Security not only protects sensitive information but also enhances your operational efficiency.