7 Must-Have Permissions Features in QA Platforms
-
Bella Williams
- 10 min read
In the evolving landscape of quality assurance, understanding Essential QA Permissions is crucial for fostering trust and security. As more organizations rely on automated systems, the need for robust permissions features becomes increasingly apparent. These features not only facilitate smooth workflows but also protect sensitive data, ensuring compliance with regulations.
Effective management of permissions can significantly enhance operational efficiency and maintain data integrity. By implementing comprehensive access controls and customizable options, QA platforms can empower users while safeguarding critical information. This introduction sets the stage for examining the must-have features of permissions in QA platforms, providing a foundation for improved quality assurance practices.
Analyze & Evaluate Calls. At Scale.
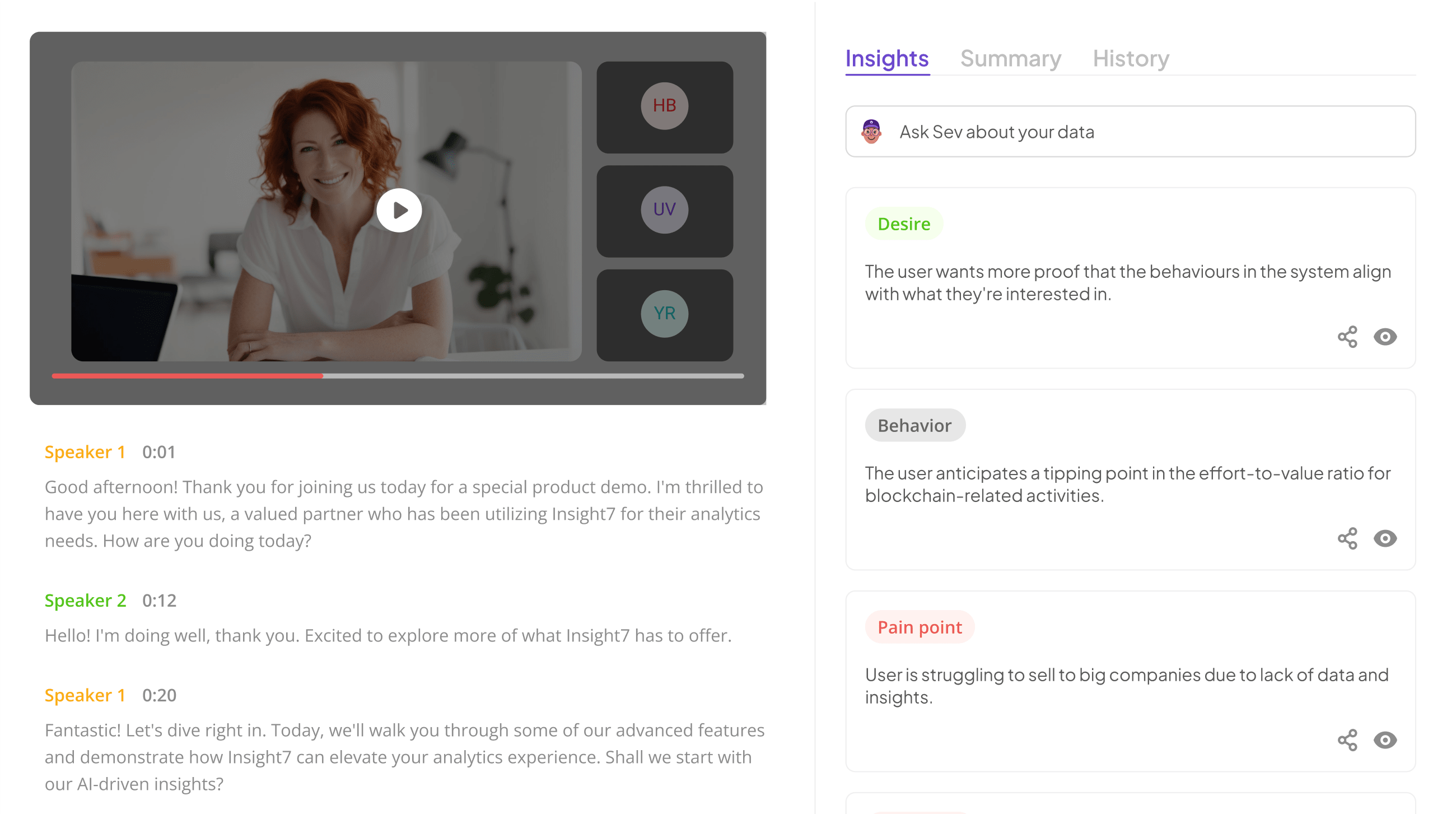
Understanding Essential QA Permissions
Essential QA Permissions are fundamental for effective quality assurance in any organization. They ensure that the right individuals have access to specific features within QA platforms, fostering both collaboration and security. Clearly defined permissions facilitate a streamlined workflow, enabling teams to focus on quality without the interruptions of access issues.
First, user access control is crucial. It empowers administrators to create role-based access, ensuring only authorized personnel can execute critical tasks. Customizable permissions allow organizations to tailor access to suit varying team needs, enhancing operational efficiency. Next, data security and privacy are vital components. Implementing robust encryption protocols safeguards sensitive information, while audit trail logging provides transparency, keeping track of who accessed what data and when. By understanding and utilizing these essential QA permissions, organizations can bolster their quality assurance processes, reducing risks and improving outcomes.
Defining Permissions in QA Platforms
Defining permissions in QA platforms is crucial for maintaining the integrity and functionality of quality assurance processes. Effective management of these permissions ensures that the right individuals have access to specific resources and information. With Essential QA Permissions, teams can define and implement user roles, allowing for seamless workflows. Each user can be granted access based on their responsibilities and needs, enhancing accountability within the organization.
Moreover, understanding permissions extends to data security, as controlling access to sensitive information is paramount. Organizations must consider how to safeguard data while ensuring that team members can efficiently perform their tasks. By implementing role-based access and customizable permissions, QA platforms can mitigate risks associated with unauthorized access. Ensuring clarity around these permissions empowers teams to operate more effectively, fostering a culture of trust and transparency.
Importance of Permissions in Quality Assurance
In the realm of quality assurance, the importance of permissions cannot be overstated. Ensuring proper access controls is critical for maintaining data integrity and security. Essential QA permissions facilitate structured workflows, enabling teams to operate efficiently without the risk of unauthorized access to sensitive information. When well-implemented, these permissions help foster a culture of accountability and trust within organizations.
Moreover, assigning the right permissions protects the organization from potential data breaches and compliance risks. This involves establishing definitive roles and responsibilities, which streamlines operations and mitigates the likelihood of errors. Additionally, clear permission structures empower team members by granting them the access they need while ensuring that critical data remains secure. Ultimately, a robust permission framework is vital not only for operational efficiency but also for preserving the trust of clients by upholding data privacy and compliance standards.
Extract insights from interviews, calls, surveys and reviews for insights in minutes
Essential QA Permissions for Seamless Workflows
Effective quality assurance (QA) processes rely heavily on essential QA permissions that facilitate seamless workflows. These permissions ensure that team members have the access they need to perform their roles without unnecessary hurdles. A clear structure of user access control is crucial for optimizing productivity and maintaining data integrity.
To achieve this, platforms should offer role-based access, which assigns permissions based on user roles within the organization. Additionally, customizable permissions allow flexibility to adapt to specific project requirements or employee responsibilities. Prioritizing data security and privacy is also vital. This can be achieved through advanced encryption protocols and robust audit trail logging, which monitor and track user interactions within the system. By integrating these essential QA permissions, organizations can create efficient, secure workflows that drive quality improvements.
User Access Control
User access control is crucial for maintaining security and efficiency in QA platforms. It governs how users interact with the system and the level of access they have to sensitive data. By implementing strong access control measures, organizations can ensure that only authorized personnel can view or modify critical information, reducing the risk of errors and breaches.
Role-based access is an effective way to streamline user management. It allows administrators to assign permissions based on user roles, ensuring that each team member has the appropriate access level for their tasks. Additionally, customizable permissions enable organizations to tailor access settings according to specific project needs. This flexibility is key for establishing a secure environment that accommodates various workflows while also ensuring compliance with data protection regulations. By prioritizing these essential QA permissions, organizations safeguard their data while enhancing team productivity.
Step 1: Role-Based Access
In the world of quality assurance, step one in establishing effective permissions is role-based access. This approach ensures that every team member has access tailored to their specific responsibilities. By defining roles clearly, organizations can limit exposure to sensitive information while empowering users to perform their tasks efficiently.
Implementing role-based access involves several key aspects. First, identify the different roles within the QA process, such as testers, managers, and administrators. Next, assign permissions based on these roles to avoid confusion and ensure compliance with privacy standards. Finally, regularly review and update these roles to accommodate any changes in team structure or project needs. By prioritizing role-based access, you not only safeguard essential QA permissions but also streamline workflows, making your QA process more effective and secure.
Step 2: Customizable Permissions
Customizable permissions play a pivotal role in ensuring that the right individuals have access to the appropriate features in QA platforms. With essential QA permissions, users can tailor their access according to various roles within the organization. This flexibility is vital for optimizing workflows and maintaining data security while empowering team members to perform their tasks effectively.
To implement customizable permissions, start by defining user roles based on project needs. Next, determine the level of access each role requires—ranging from read-only permissions to full administrative rights. Fine-tuning these settings ensures that sensitive data remains protected while enabling team collaboration. Additionally, regularly review and update permissions as project requirements or personnel change. This process not only enhances the user experience but also reinforces a secure environment, thus fostering trust and efficiency in quality assurance efforts.
Data Security and Privacy
Data security and privacy are paramount in today’s digital landscape, especially within QA platforms. Implementing strong data protection measures ensures that sensitive information remains confidential and is handled appropriately, safeguarding both users and organizations. A well-designed QA platform must prioritize protections that prevent unauthorized access, data breaches, and misuse of personal information.
Two essential features to enhance security and privacy are encryption protocols and audit trail logging. Encryption protocols protect data during transfers, making it unintelligible to unauthorized users. This step is crucial for maintaining the integrity of sensitive data. Additionally, audit trail logging records all access and modifications made to data. This accountability measure helps trace any unauthorized actions and provides transparency, fostering trust among users. By focusing on these elements, QA platforms can effectively secure essential data while promoting a culture of privacy and respect for user information.
Step 1: Encryption Protocols
To ensure data security and privacy, Step 1: Encryption Protocols is crucial for any quality assurance (QA) platform. Effective encryption protocols safeguard sensitive information from unauthorized access during storage and transmission. They serve as the first line of defense, protecting user data from potential breaches and ensuring compliance with regulatory standards.
Implementing robust encryption methods involves multiple considerations. First, data encryption at rest encrypts stored data, protecting it from physical theft. Second, data in transit is secured through protocols such as SSL/TLS, which safeguards information during transmission across networks. Third, employing strong encryption algorithms enhances security, ensuring that even if data is intercepted, it remains unreadable to unauthorized users. Adopting these practices is essential for maintaining trust in the platform and provides a secure environment for users navigating their QA processes.
Step 2: Audit Trail Logging
In Step 2: Audit Trail Logging, it's essential to grasp how logging activities can enhance quality assurance processes. An effective audit trail records every action taken within the QA platform, ensuring transparency and accountability. This feature not only tracks user activities but also captures data modifications, helping teams identify trends and anomalies that may affect project quality.
Moreover, maintaining an audit trail strengthens compliance with industry standards and regulations, which is particularly crucial in sectors prone to scrutiny. With this functionality in place, organizations can review historical data and user interactions, facilitating more accurate quality assessments. Ultimately, audit trail logging serves as a backbone for essential QA permissions, fostering a secure environment where teams can operate efficiently and responsibly.
Conclusion: Integrating Essential QA Permissions for Success
Integrating essential QA permissions is crucial for driving success in quality assurance processes. These permissions foster greater collaboration among teams, ensuring that the right individuals have access to necessary information while maintaining data security. By streamlining access rights and enhancing user control, organizations can facilitate smoother workflows, ultimately improving product quality.
Implementing these features not only empowers team members but also encourages accountability within the QA process. As teams adapt to changing project needs, prioritizing these essential QA permissions will position organizations for future success and innovation in quality assurance. Embracing these elements is not merely beneficial; it is vital for achieving excellence in today’s competitive environment.