How to Vet QA Tools for Security, Compliance, and Data Governance
-
Bella Williams
- 10 min read
Quality assurance (QA) tools are vital in today's digital environment, ensuring that products meet security, compliance, and data governance standards. When organizations consider integrating new QA tools, it's essential to carry out comprehensive QA tools vetting. This process not only safeguards sensitive information but also fortifies compliance with industry regulations.
Initiating this vetting journey requires a clear understanding of the potential risks associated with the tools being assessed. By evaluating their security features, including encryption and certification, you can gauge their ability to protect data effectively. Compliance with relevant regulations further enhances the trustworthiness of these tools, supporting a structured approach to data governance while aligning with best practices for security.
Analyze & Evaluate Calls. At Scale.
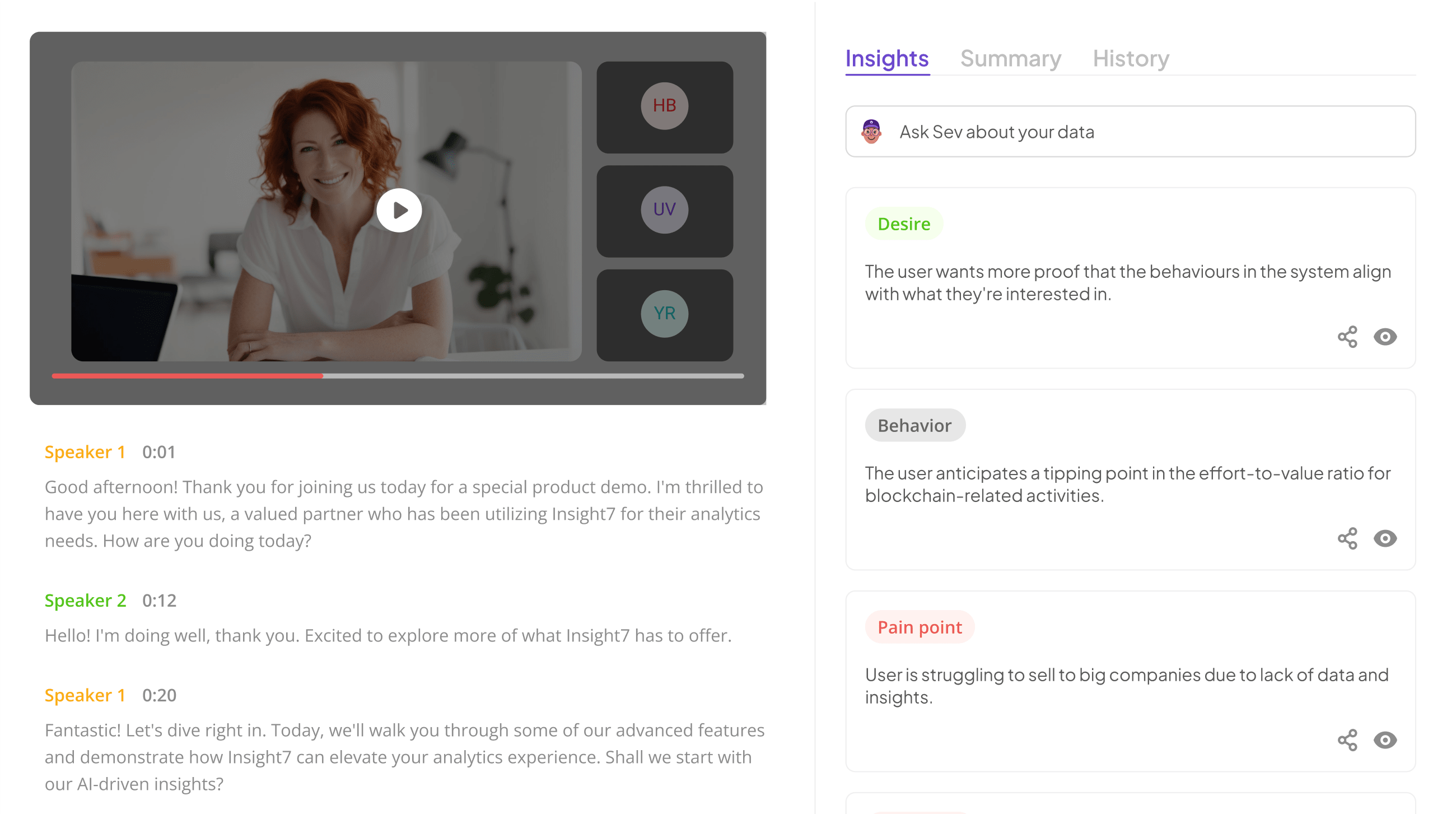
Essential Steps for QA Tools Vetting in Security
To effectively conduct QA tools vetting in security, begin by identifying specific security requirements tailored to your organization. Start by assessing the scope of data handled, as this highlights the types of information at risk. Understanding the data flow will help in pinpointing security checkpoints essential for your systems. By recognizing vital security elements, you set a groundwork that ensures robust protection against potential threats.
Next, move on to evaluating the security features of potential QA tools. This includes analyzing encryption standards to safeguard data both in transit and at rest. Always investigate security certifications, as these demonstrate the reliability and compliance of the tools with industry regulations. The integration of these steps creates a thorough vetting process, ultimately ensuring that the chosen QA tools enhance your security posture while maintaining compliance and data governance.
Identifying Security Requirements
To ensure your QA tools align with your security needs, identifying security requirements is critical. Start by assessing the scope of the data you handle. Understanding whether you work with sensitive personal information, financial records, or proprietary business data informs the level of security required.
Next, pinpoint the security checkpoints necessary for your operations. These may include authentication processes, data encryption standards, and user access controls. By establishing these requirements, you create a solid foundation for your QA tools vetting process. This approach ensures that all evaluated tools meet your security expectations, contributing to compliance and data governance while minimizing risks associated with data breaches. Identifying security requirements is an instrumental step in selecting QA tools that not only enhance quality assurance but also reinforce your overall security posture.
- Step 1: Assess the scope of data handled
To effectively vet QA tools, the first step is to assess the scope of data handled. Begin by cataloging all types of data your organization processes, which can range from personal information to sensitive business data. Understanding the volume and variety of data is crucial for recognizing specific security and compliance needs associated with various QA tools.
Next, consider the channels through which data moves. Is it transmitted, stored, or processed in real-time? Identifying these aspects helps determine the necessary security precautions and compliance measures. Assessing data scope also allows you to pinpoint the specific regulatory requirements applicable to your business, which can vary by industry. By taking these initial steps, you will establish a solid foundation to ensure that the selected QA tools meet your organization's security, compliance, and data governance standards effectively.
- Step 2: Pinpoint security checkpoints required
In the process of QA tools vetting, pinpointing the required security checkpoints is crucial for ensuring data protection. Start by identifying essential security measures relevant to your organization's operational framework. Focus on areas such as data encryption, access control, and audit logging. By highlighting these specific checkpoints, teams can ensure the selected tools meet necessary security standards.
Additionally, evaluate whether the tools comply with industry regulations and frameworks. Consider aspects such as user authentication, data breach response plans, and third-party risk management. Logically assessing these checkpoints will empower stakeholders to gauge the overall security posture of potential QA tools. Ultimately, this meticulous approach to QA tools vetting will help maintain compliance and bolster data governance efforts. With the right checkpoints in place, organizations can confidently move forward in their decision-making process.
When it comes to QA tools vetting for security, compliance, and data governance, identifying your security requirements is critical. Start by assessing the scope of the data your organization handles. This involves understanding what types of data, such as personally identifiable information or sensitive company data, you need to protect. Next, pinpoint the specific security checkpoints required for your operations. Consider regulatory requirements and industry best practices that may dictate additional security measures.
Following this, a thorough evaluation of the security features in potential QA tools is necessary. Focus on analyzing encryption standards, as they determine how effectively data is protected during transmission and storage. Additionally, investigating the security certifications held by these tools can offer insights into their compliance with industry standards. Together, these steps form the foundation of your QA tools vetting process, ensuring better alignment with security and compliance needs.
Evaluating Security Features
When evaluating security features of QA tools, it’s crucial to thoroughly assess their capabilities to protect sensitive data. Begin by analyzing the encryption standards employed by these tools. Strong encryption protects data both in transit and at rest, minimizing risks during data handling and storage. If a tool lacks robust encryption mechanisms, it may expose your organization to potential breaches.
Next, investigate the security certifications the QA tools possess. Certifications from reputable organizations can signify a tool's adherence to industry security standards. Look for compliance with standards such as ISO/IEC 27001 or SOC 2. These certifications ensure that the tool undergoes regular independent assessments, enhancing trust in its security reliability. By focusing on encryption and security certifications, organizations can make informed choices during the QA tools vetting process, safeguarding their assets while ensuring compliance with data governance regulations.
- Analyze encryption standards
When analyzing encryption standards, it's crucial to understand their role in protecting sensitive data within QA tools. Reliable encryption safeguards data during transmission and storage, making it harder for unauthorized parties to access it. Start by identifying the encryption protocols employed by the QA tools under consideration. Standard protocols like AES (Advanced Encryption Standard) are essential, as they provide strong, industry-recognized encryption mechanisms.
Next, evaluate whether the QA tools offer end-to-end encryption. This ensures data remains encrypted from the source to the destination, enhancing security. Additionally, verify if the tools comply with relevant data protection regulations, which may mandate specific encryption requirements. Understanding the cryptographic practices used in QA tools vetting and how they align with your organization's security framework is vital. Therefore, assessing encryption standards is essential for building trust and ensuring data governance while adopting QA tools.
- Investigate security certifications
Security certifications serve as a critical benchmark in evaluating the integrity and safety of QA tools. When vetting these tools, it is essential to investigate which certifications they possess. Understanding certifications such as ISO 27001, SOC 2, and PCI DSS can significantly influence your decision. These certifications guarantee that the tool meets established security standards, ensuring compliance with various regulatory requirements.
When delving into certifications, focus on the relevance of each one to your unique data governance needs. For instance, if the tool will manage sensitive financial information, certifications like PCI DSS are particularly essential. Additionally, verifying regular updates and renewals of these certifications can indicate an ongoing commitment to security. A thorough evaluation of these security certifications will not only help in the vetting process but also bolster your confidence in the selected QA tools to protect your organization’s data effectively.
Extract insights from interviews, calls, surveys and reviews for insights in minutes
QA Tools Vetting for Compliance Needs
When engaging in QA tools vetting for compliance needs, it's crucial to begin by establishing a clear compliance checklist. Start by identifying the specific regulations that govern your industry, which often vary significantly across sectors. For example, healthcare, finance, and education each have unique compliance requirements that must be addressed during the evaluation process. Creating a detailed list of required compliance features will help ensure that the chosen QA tools meet these standards effectively.
💬 Questions about How to Vet QA Tools for Security, Compliance, and Data Governance?
Our team typically responds within minutes
Next, reviewing compliance support offered by various tools becomes essential. Assess how each tool assists in maintaining compliance through features such as automated reporting, audit trails, and data protection mechanisms. Pay special attention to user feedback regarding compliance management functionalities, as this can provide insight into the tool's real-world effectiveness. By incorporating these strategies, organizations can make informed decisions that bolster security, compliance, and data governance across their operations.
Compliance Checklist Creation
Creating a compliance checklist is a vital step in vetting QA tools for security and regulatory adherence. To start, identify industry-specific regulations that your organization must comply with, such as GDPR, HIPAA, or PCI DSS. These regulations dictate the necessary features your QA tools must offer, such as data encryption, user access control, and audit trails. Ensuring these criteria are clearly documented forms the backbone of your compliance checklist.
Next, list the required compliance features for your QA tools. This may include criteria for recording and analyzing interactions, maintaining data integrity, and ensuring user awareness of compliance standards. Furthermore, prioritize these features based on their significance to your industry and operational needs. By effectively creating this compliance checklist, you streamline the vetting process, ensuring that the selected QA tools not only meet security objectives but also adhere to regulatory and governance frameworks.
- Identify industry-specific regulations
When engaging in QA Tools vetting, identifying industry-specific regulations is crucial for ensuring compliance and security. Each industry has unique standards and regulatory frameworks that dictate how data must be managed and protected. Organizations must first familiarize themselves with the most relevant regulations, such as GDPR for data privacy, HIPAA for healthcare, or PCI DSS for payment processing. Understanding these regulations will help determine the necessary features and certifications your QA tools must possess to meet compliance requirements.
Following this identification phase, evaluate how well potential QA tools align with these regulations. It's essential to consider their built-in compliance features, such as data encryption and access controls, alongside their ability to provide audit reports and maintain data integrity. By aligning your QA tool choices with industry-specific regulations, you ensure robust data governance while mitigating risks associated with non-compliance, fostering a secure and trustworthy environment for data management.
- List required compliance features
Identifying the necessary compliance features is crucial in QA tools vetting. To ensure robust data governance, compile a set of features that align with your industry regulations. Key compliance areas typically include data protection, audit trails, and user access controls. Each of these features plays a significant role in safeguarding sensitive information and ensuring adherence to legal obligations.
Moreover, consider features that facilitate reporting and monitoring. Automated alerts for compliance breaches can significantly enhance your oversight capabilities. It's also important to assess whether the tool supports specific compliance frameworks relevant to your industry, such as GDPR or HIPAA. This due diligence during the vetting process not only safeguards your organization but also builds trust with stakeholders. Thus, a comprehensive checklist of compliance features should be integral to your QA tools vetting process, ensuring that all essential criteria are met effectively.
Reviewing Compliance Support in Tools
Understanding compliance support in QA tools is crucial for ensuring adherence to industry regulations. When evaluating QA tools, thoroughly assess the compliance capabilities they offer. This involves not only identifying the regulations specific to your industry but also confirming that the tools can meet those requirements effectively. Start by checking if the tools provide flexibility in adapting to various compliance mandates, such as GDPR or CFTC, allowing for adjustments as necessary.
Next, ensure that the tools can automate compliance checks. Automated features reduce the risk of human error and facilitate continuous monitoring of adherence to compliance standards. Look for features that allow for keyword and phrase analysis, enabling rapid identification of potentially non-compliant content. Having real-time insights helps teams make informed decisions swiftly, promoting operational efficiency while maintaining compliance. Thoroughly vetting these aspects during your QA tools vetting process will bolster your organization’s overall compliance framework.
- insight7
When evaluating QA tools, understanding their compliance support is integral to the decision-making process. QA tools vetting involves a thorough examination of features designed to meet specific industry regulations, ensuring that they adhere to necessary standards. Begin with a compliance checklist that outlines relevant regulations specific to your industry. This ensures that the tools you consider not only meet your needs but also operate within the confines of legal requirements.
Next, review the compliance support frameworks that each tool offers. Look for specific features that assist in maintaining compliance, such as audit trails, documentation support, and user access controls. These functionalities help streamline reporting processes and provide transparency into how data is managed. By prioritizing compliance support during QA tools vetting, organizations can mitigate risks associated with data governance, ensuring a more secure operational environment.
- Tool A
When considering Tool A in the QA tools vetting process, it is essential to evaluate its capabilities for security, compliance, and data governance needs. A well-rounded examination of this tool involves assessing how it aligns with your organization’s unique security requirements and compliance obligations. Security features such as encryption standards and user authentication protocols are critical, as they influence the tool's ability to protect sensitive data.
In addition to security features, it is important to analyze Tool A’s compliance support. This includes evaluating its compatibility with industry-specific regulations and the flexibility it offers for customization based on client needs. For instance, each client may have distinct scripts and scorecards that should be effectively supported by the tool. Through a thorough understanding of these aspects, organizations can confidently determine if Tool A is a viable option within their QA tools vetting process for enhanced security and compliance.
- Tool B
Tool B plays a critical role in the QA tools vetting process, especially regarding security and compliance. When evaluating Tool B, ensure it aligns with your organization’s security requirements and compliance needs. Start by understanding its features. Does it offer robust encryption to protect sensitive data during transmission? Additionally, consider its compliance certifications. Tools that adhere to industry standards can robustly support your data governance initiatives.
Moving further, examine Tool B’s customization capabilities. Each client may require different configurations to meet specific compliance standards. Therefore, ensure Tool B offers flexible options that cater to individual client needs. Furthermore, assess the tool's ability to provide regular updates and support for evolving regulations, guaranteeing your organization remains compliant over time. By taking these steps, Tool B can significantly enhance your QA tools vetting process, ensuring that you choose a solution that helps manage risks effectively while fostering trust with your stakeholders.
- Tool C
When considering Tool C for QA tools vetting, it's essential to evaluate its capabilities against your specific requirements for security, compliance, and data governance. Tool C offers a suite of features that can effectively address the critical areas necessary for ensuring adherence to industry standards and protecting sensitive data. Start by examining its security capabilities, particularly its encryption methods and any relevant certifications that demonstrate compliance with regulatory frameworks.
Next, assess Tool C's robustness in managing compliance requests and its ability to handle various data types. Investigate how it integrates with existing systems and its flexibility in adapting to changing compliance requirements. Additionally, understanding how Tool C updates its features to keep pace with new regulations is crucial for long-term procurement. This assessment will guide your QA tools vetting process, ensuring Tool C aligns with your operational protocols and enhances overall compliance efforts.
Conclusion: Effective QA Tools Vetting for Holistic Data Management
In conclusion, effective QA tools vetting is essential for achieving comprehensive data management practices. Organizations must prioritize security, compliance, and data governance during the selection process to ensure that their chosen tools safeguard their information effectively. This requires a clear understanding of specific security requirements and industry regulations that apply to their operations.
Moreover, thoroughly evaluating the security features of potential QA tools is crucial. Consider aspects such as encryption standards and certifications to assess reliability. By implementing a robust QA tools vetting process, decision-makers can foster a secure and compliant environment that nurtures holistic data management aligned with organizational goals.
💬 Questions about How to Vet QA Tools for Security, Compliance, and Data Governance?
Our team typically responds within minutes