How to Share Google Sheets Call Logs Securely Across Teams
-
Bella Williams
- 10 min read
When teams collaborate on call logs using Google Sheets, the need for secure Google Sheets sharing becomes paramount. Sensitive data such as call transcripts and notes must be protected from unauthorized access, ensuring compliance with data protection regulations. A breach can expose not only pivotal business insights but also compromise personal information, leading to significant operational risks.
To establish a secure sharing environment, it's vital to understand the basic principles of data security. These include reviewing current sharing settings and granting access levels according to necessity. By employing best practices and utilizing tools designed for data protection, teams can enhance security, streamline collaboration, and safeguard sensitive information effectively while working with shared resources.
Analyze & Evaluate Calls. At Scale.
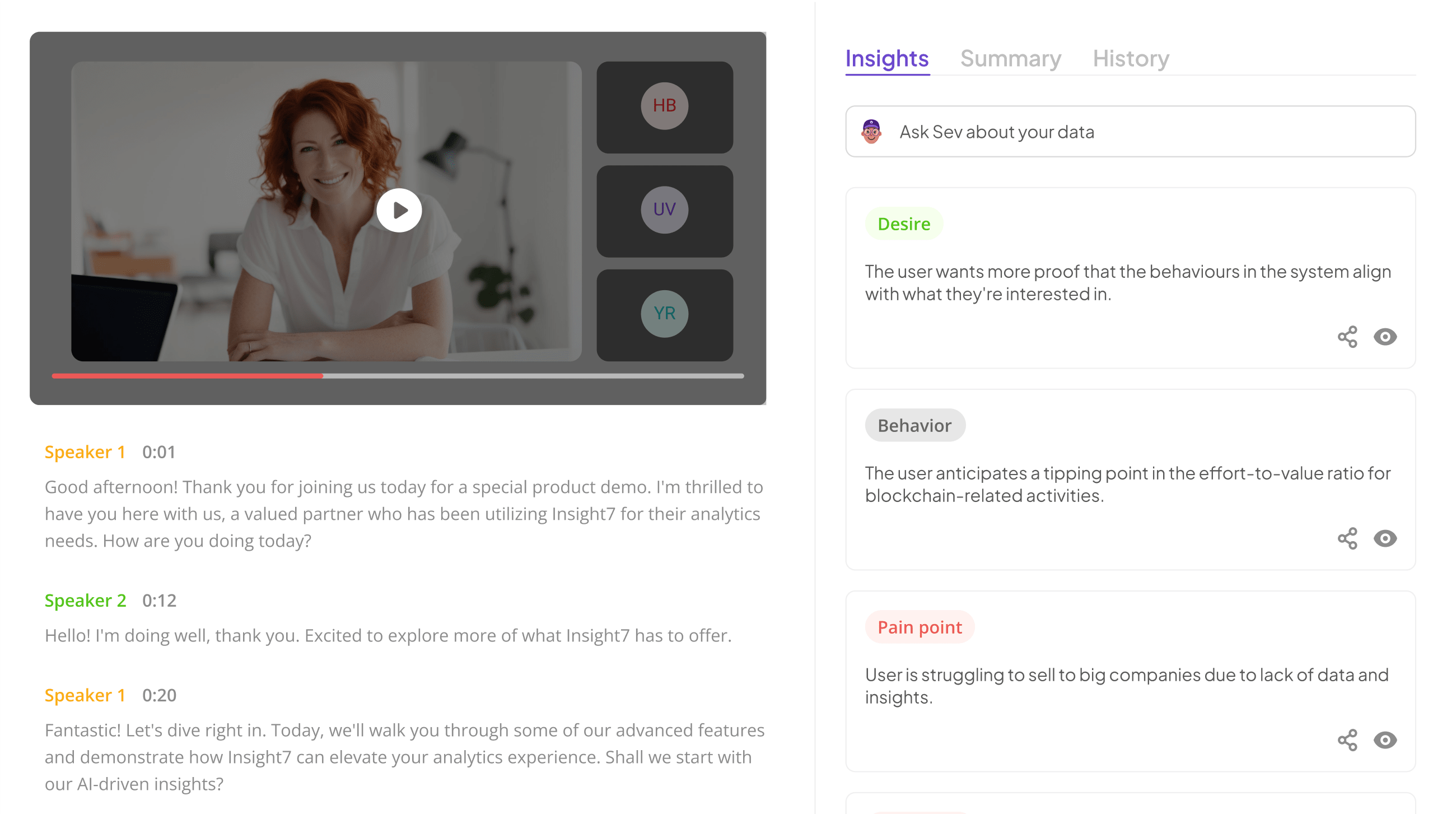
Understanding Secure Google Sheets Sharing Basics
Understanding the basics of secure Google Sheets sharing is essential for effectively managing sensitive data, such as call logs. Secure Google Sheets sharing involves a strategic approach to permissions and access control. Users must recognize that every shared sheet can be a potential entry point for unauthorized access. Thus, understanding how to safeguard your documents is paramount for team collaboration.
When sharing Google Sheets, consider the various permissions settings available, including viewing, commenting, and editing. Each role should align with an individual's responsibilities within the team. Additionally, using link sharing cautiously prevents unintentional exposure of sensitive information. Collaborating securely not only requires understanding the tools but also establishing trust among team members. By mastering these basics, you ensure that your data remains confidential and accessible only to authorized personnel.
Importance of Secure Sharing for Call Logs
Sharing call logs securely is crucial in maintaining the integrity and confidentiality of sensitive information. The importance of secure sharing for call logs cannot be underestimated, especially in collaborative environments. By ensuring that data is shared securely, teams can protect themselves from potential breaches and misuse of information. Secure Google Sheets sharing not only safeguards customer details but also enhances the accountability of team members who access this data.
When logs are shared without adequate security measures, the risks escalate significantly. Unauthorized access can lead to data leaks, which may compromise client trust and legal compliance. Consequently, teams must adopt robust security protocols to ensure that sensitive information is accessed only by those who need it. By prioritizing secure sharing practices, organizations can effectively minimize risks while fostering a collaborative atmosphere where data integrity is upheld at all times.
Risks of Inadequate Security Measures
Inadequate security measures when sharing Google Sheets can expose sensitive call logs to unauthorized individuals, leading to significant risks. Firstly, data breaches can occur, compromising the confidentiality of sensitive information. This not only affects team trust but can also lead to compliance violations and potential legal repercussions. Additionally, without adequate security, employees may inadvertently share information with unintended recipients, causing confusion and miscommunication.
Moreover, the lack of security increases the chances of malicious attacks, such as phishing or ransomware, which can disrupt operations and lead to financial loss. It's crucial to recognize that secure Google Sheets sharing is not just a technical requirement but a key component of maintaining business integrity. Implementing robust security practices ensures that team collaboration remains effective while protecting against these considerable risks. Thus, prioritizing security is essential for safeguarding valuable data and maintaining operational continuity.
Best Practices for Secure Google Sheets Sharing
When engaging in secure Google Sheets sharing, especially for sensitive call logs, it's crucial to implement best practices to safeguard your data. Start by reviewing current sharing settings to understand who has access and what permissions they hold. Doing so helps in identifying any unauthorized access or outdated permissions that may pose a risk to your data.
Next, establish appropriate access levels tailored to team members’ needs. Only grant edit permissions to those who require it, while opting for view-only access for others. It is also important to utilize link sharing cautiously; ensuring that links are only shared with trusted individuals and that access is set to expire when necessary can further enhance security. Finally, adopting advanced security features offered by tools like Google Workspace can bolster your protective measures, providing an additional layer of security for all team members involved.
Step-by-Step: How to Set Permissions
To ensure secure Google Sheets sharing, the first step is to review your current sharing settings. Open your Google Sheets document and click on the "Share" button in the top right corner. You will see a list of people who currently have access. This helps you identify any potential vulnerabilities. Always ensure that only necessary team members can view or edit the call logs.
Next, establish appropriate access levels for each user. You can choose between view-only, comment access, or editing rights. Assigning the right level of access prevents unauthorized alterations and maintains the integrity of your call logs. Lastly, utilize link sharing with caution. When enabling link sharing, restrict access to only those with the link, and preferably limit it to view-only mode. This step helps you maintain tighter control over your data while facilitating necessary collaboration among teams.
- Review Current Sharing Settings
To ensure Secure Google Sheets Sharing, it is crucial to begin by reviewing current sharing settings. This process helps you assess who currently has access to your call logs and at what level. Open your Google Sheets document and navigate to the “Share” button in the top-right corner. Here, you can see the list of users who have access, along with their permission levels, such as viewer, commenter, or editor. Identifying who can edit or view sensitive data is essential for maintaining the integrity of your call logs.
Next, evaluate whether these permissions align with your sharing policy. If team members no longer require access, remove them to limit potential risks. Equally, if certain individuals need elevated permissions, ensure this is done judiciously. Remember that sharing settings can significantly impact the security of sensitive information. By taking these steps, you are ensuring a foundation for sharing call logs securely across teams while minimizing unauthorized access.
- Establish Appropriate Access Levels
Establishing appropriate access levels is crucial for maintaining the security of shared Google Sheets, especially for sensitive call logs. To achieve secure Google Sheets sharing, designate specific roles for each team member. Clearly define who needs view-only access, who requires comment privileges, and who should have editing rights. This granular approach not only protects sensitive information but also ensures team members can contribute effectively without compromising data integrity.
Consider implementing access levels based on project roles. For instance, managers may need full editing capabilities, while junior team members could benefit from view-only permissions. Regularly review and update these access levels to adapt to evolving team structures or project demands. By establishing appropriate access levels, you promote a culture of security and collaboration, allowing teams to work efficiently while safeguarding critical data.
- Utilize Link Sharing with Caution
Link sharing can be a convenient feature in Google Sheets, but utilizing it without caution can lead to significant security risks. When sharing call logs across teams, it’s essential to ensure that sensitive information remains protected. A simple link could inadvertently reach unintended recipients if not handled correctly. As a precaution, always evaluate the sharing settings before distributing any link.
To safeguard data effectively, consider these guidelines. First, establish a clear understanding of who needs access and why. Limit permissions to only those team members who truly require it, ensuring that they can view or edit the document based on their role. Secondly, consider using expiration dates for links or revoking access once the necessary collaboration is complete. By taking these steps, you will ensure that your Google Sheets sharing is aligned with secure practices and protects valuable information.
Leveraging Tools for Enhanced Security
To enhance security while sharing Google Sheets call logs, it's essential to integrate various tools and features designed for this purpose. First, understanding how to secure Google Sheets sharing can prevent unauthorized access and data breaches. Tools like Secure Sheet and Authomator aid in establishing strict access controls, ensuring that only designated team members can view sensitive information.
Google Workspace also offers built-in security features, such as two-factor authentication and activity tracking. Utilizing these features not only deters unauthorized access but also provides a clear audit trail. Sheetgo can automate data transfers and maintain seamless updates while ensuring security protocols are maintained throughout the process. By implementing these tools, teams can enhance collaboration without compromising data integrity.
Incorporating such measures is more than a technical requirement; it’s a cornerstone of responsible data management. Secure Google Sheets sharing ultimately fosters a culture of trust and efficiency within teams.
insight7: Leading Tool for Secure Collaboration
Secure Google Sheets Sharing can significantly enhance team collaboration while ensuring sensitive information remains protected. In this digital age, maintaining confidentiality in shared documents is paramount. Insight7 emerges as a leading tool for secure collaboration, providing robust features that bolster data security. By utilizing advanced encryption and user-access controls, Insight7 ensures that only authorized individuals can access shared call logs, safeguarding against unauthorized breaches.
To achieve secure collaboration, it’s essential to implement best practices. First, establish clear permission settings to determine who can view or edit the documents. Second, regularly review access levels and adjust them based on project needs. Finally, leverage integrated security features offered by tools like Insight7 to ensure a seamless sharing experience. Emphasizing these strategies can transform how teams collaborate and protect their crucial data while sharing Google Sheets call logs.
Google Workspace Security Features
Google Workspace provides a comprehensive suite of security features designed to ensure safe collaboration, particularly when it comes to sharing sensitive documents like Google Sheets call logs. One of the key elements is user access control, which allows administrators to set permissions, determining who can view, comment, or edit the sheets. This level of granularity is crucial for maintaining confidentiality and ensuring that sensitive information is only accessible to authorized personnel.
Another feature is encryption both in transit and at rest, which safeguards data from unauthorized access. Moreover, Google Workspace facilitates activity monitoring, enabling teams to track changes and access history, which is vital for accountability. By understanding and leveraging these robust security features, teams can implement secure Google Sheets sharing practices, thereby enhancing data protection while fostering collaboration across different departments. Embracing these tools is essential for maintaining integrity and trust when handling sensitive call log data.
Secure Sheet
Secure Google Sheets Sharing is essential for ensuring that sensitive data, such as call logs, remains confidential while being shared across teams. By using appropriate security measures, organizations can prevent unauthorized access and maintain data integrity. A Secure Sheet is one that complies with best practices, allowing users to collaboratively work while keeping their information secure.
To create a Secure Sheet, it’s vital to review current sharing settings, establish access levels based on roles, and utilize link-sharing features judiciously. Organizations should limit editing rights to those who need them and regularly audit access permissions to ensure data is only available to relevant parties. Employing tools like Google Workspace security features can further enhance data protection. By prioritizing secure sharing methods, teams can facilitate collaboration while confidently safeguarding their sensitive information.
Authomator
Authomator plays a pivotal role in achieving secure Google Sheets sharing, especially for call logs that contain sensitive information. By implementing automation for access control and monitoring, teams can streamline their sharing processes while maintaining data integrity. Authomator allows users to set specific permissions and automatically manage who can view or edit shared sheets, thus reducing the risk of unauthorized access.
With Authomator, organizations can enforce a standardized sharing protocol that enhances accountability. This automation minimizes human error and ensures that only designated team members can access sensitive call log data. Leveraging such tools not only benefits the security of Google Sheets sharing but also fosters a culture of trust and collaboration within teams. It’s essential to adopt innovative solutions like Authomator to safeguard confidential information while allowing for seamless teamwork.
Sheetgo
Sheetgo serves as a powerful tool for enhancing the secure sharing of Google Sheets, particularly when managing call logs across teams. By creating automated workflows, it allows teams to share data effortlessly while maintaining control over who has access. This not only reduces the risk of data leaks but also ensures that all team members have the most up-to-date information at their fingertips.
Utilizing Sheetgo, users can set up pipelines that connect various Google Sheets, consolidating call log data in a secure manner. Each team can be assigned specific permissions, allowing for customized access levels. This means that sensitive data remains protected while still promoting collaboration between departments. In sum, Sheetgo offers an efficient solution that simplifies secure Google Sheets sharing, ensuring that teams work with accurate and well-managed call log data.
Conclusion: Safeguarding Data with Secure Google Sheets Sharing
To ensure effective collaboration while protecting sensitive information, adopting secure Google Sheets sharing practices is essential. By implementing the right permissions and utilizing security features, teams can guard against unauthorized access and data breaches. Start by reviewing existing settings and tailor access levels to maintain confidentiality.
When sharing call logs, consider limiting permissions to only those necessary for each team member. Always prioritize secure Google Sheets sharing to protect critical insights and uphold data integrity across your organization. With diligence and awareness, teams can successfully navigate the complexities of data sharing without compromising security.