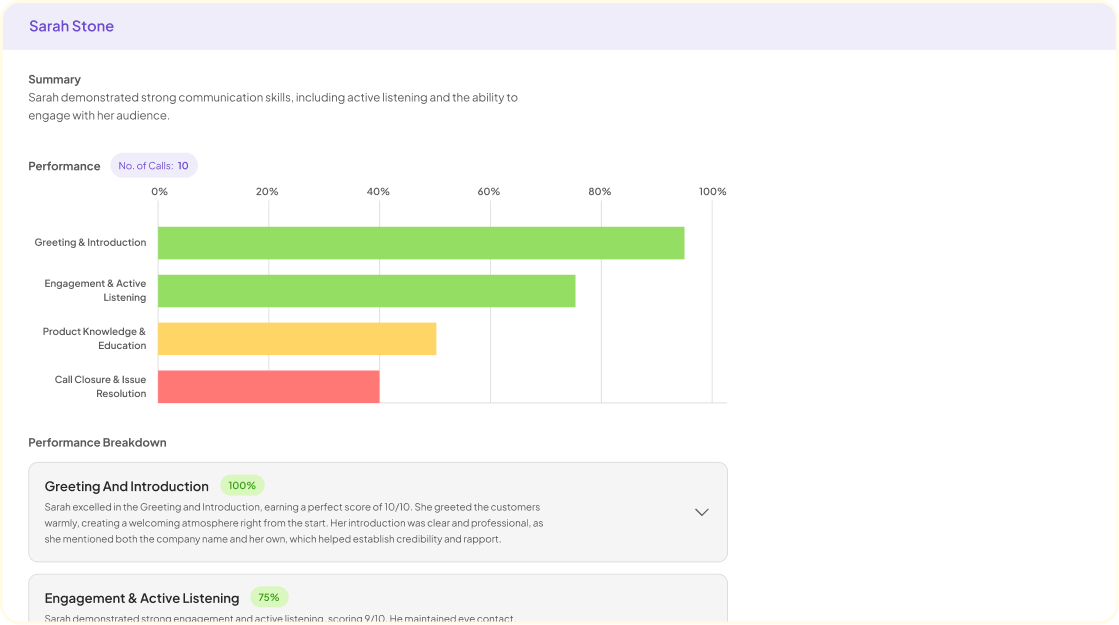
In an age where data breaches seem all too common, the importance of secure evaluation practices for call center employee evaluation forms cannot be overstated. Every interaction during customer service evaluations generates valuable insights, but these insights often include sensitive employee information. Therefore, implementing secure evaluation practices becomes imperative to protect both employee privacy and company integrity.
To begin with, secure evaluation practices encompass various strategies aimed at safeguarding evaluation data from unauthorized access. This includes investing in data encryption, which helps protect information during transmission and while stored on servers. Additionally, creating robust access controls by restricting who can view evaluation forms is essential. By making these practices foundational for your call center's evaluation process, you create a more trustworthy environment conducive to facilitating honest assessments.
Analyze & Evaluate Calls. At Scale.
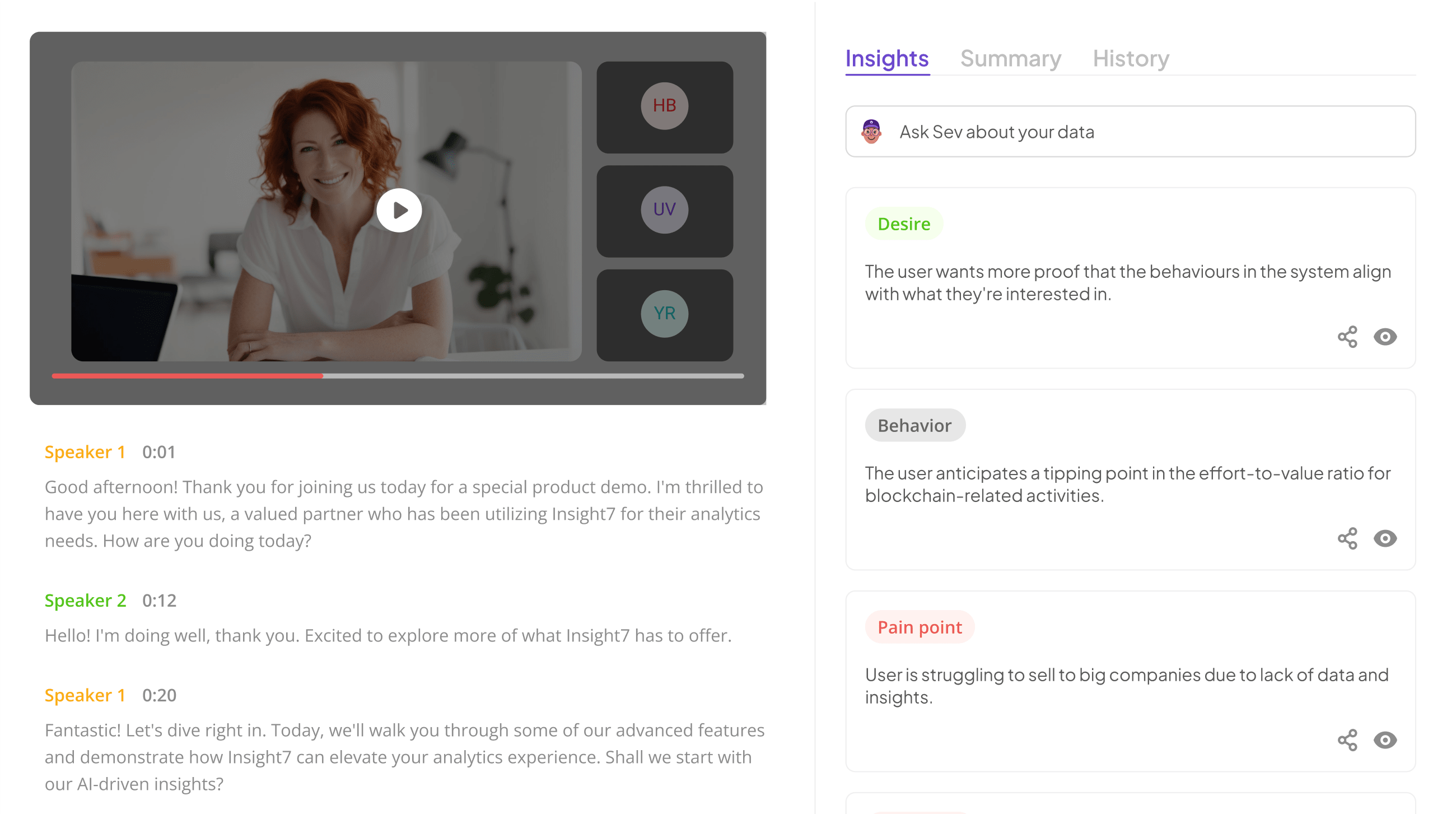
In today’s digital landscape, ensuring the security of evaluation forms is crucial for protecting sensitive employee information. This blog post explores the best practices for secure call center employee evaluation forms.
In the digital age, safeguarding evaluation forms is vital for securing sensitive employee information. Organizations that handle such data must recognize the significance of implementing secure evaluation practices to mitigate risks associated with data breaches. With the increasing technological advancements, ensuring the confidentiality of these forms is not just a regulatory requirement but also a cornerstone of employee trust and organizational integrity.
To achieve robust security, it is essential to focus on specific methodologies. First, employing data encryption techniques protects information during transmission and storage. Additionally, restricting access through authentication protocols ensures that only authorized personnel can view or alter these forms. By adopting these best practices, call centers can establish a secure environment for employee evaluations, ultimately leading to enhanced data safety and compliance with privacy standards.
Essential Secure Evaluation Practices
In the realm of evaluation forms for call center employees, embracing essential secure evaluation practices is pivotal. Start by prioritizing data protection through encryption. It ensures that sensitive employee information remains confidential both during transmission and while stored. Choose strong encryption protocols and maintain secure storage solutions to further enhance data safety.
Moreover, access control plays a vital role in safeguarding evaluation forms. By implementing multi-factor authentication, only authorized personnel can access confidential documents, significantly reducing the risk of data breaches. Regularly updating access permissions and reviewing user access can lead to robust security measures. Together, these essential secure evaluation practices not only protect data but also enhance trust within the organization, ensuring a secure environment for both employees and customers.
Data Encryption and Storage
Implementing effective data encryption and storage practices is vital to ensuring the security of call center employee evaluation forms. To begin, selecting the right encryption protocols is paramount. This process involves employing robust encryption standards such as AES (Advanced Encryption Standard) to protect sensitive data during transmission and storage. By encrypting this data, you create an additional layer of security that defends against unauthorized access.
Next, proper storage solutions are essential for maintaining data integrity. Utilize secure servers with advanced security configurations and cloud services that meet compliance standards. Make use of solutions that provide backup and recovery options, ensuring data remains protected even in unforeseen circumstances. By focusing on these secure evaluation practices, you not only safeguard sensitive employee information but also enhance trust within your organization. Prioritizing encryption and secure storage can lead to a significant reduction in potential vulnerabilities associated with data breaches.
Implementing robust encryption techniques is essential to safeguard sensitive information during transmission and while stored.
Implementing robust encryption techniques is essential to safeguard sensitive information during transmission and while stored, particularly when handling evaluation forms in a call center environment. Encryption serves as a first line of defense against unauthorized access, ensuring that sensitive data, such as employee evaluations and personal information, remain confidential. When data is encrypted, it is transformed into an unreadable format, accessible only to those possessing the correct decryption keys.
To achieve secure evaluation practices, organizations should first choose the right encryption protocols, such as AES (Advanced Encryption Standard), which provide a high level of security. Additionally, secure storage solutions, including encrypted databases, should be utilized to protect stored information. Employing these encryption strategies not only enhances data integrity but also builds trust between employees and management by ensuring their information is kept private and secure.
In summary, effective use of encryption techniques is vital in fostering secure evaluation practices, thus protecting sensitive information during transmission and storage. By committing to robust encryption methods, organizations can significantly reduce the risk of data breaches and maintain the integrity of their evaluation processes.
- Step 1: Choose the Right Encryption Protocols
Choosing the right encryption protocols is foundational in secure evaluation practices. Effective encryption ensures that sensitive employee data is protected during transmission and while in storage. Start by considering widely recognized protocols such as Advanced Encryption Standard (AES), which standardizes security for various applications. Using AES not only enhances data security but also helps comply with regulatory requirements.
Next, examine Transport Layer Security (TLS) for securing data in transit. TLS encrypts communication between servers and clients, preventing interception by unauthorized parties. Implementing secure protocols demonstrates a proactive approach to safeguarding sensitive information, fostering trust both within the organization and among employees. Ultimately, attention to encryption is crucial for the integrity of employee evaluations in call centers, ensuring that evaluations remain confidential and secure.
- Step 2: Ensure Proper Storage Solutions
Proper storage solutions are critical for maintaining the security and integrity of employee evaluation forms. These forms often contain sensitive information such as performance reviews and personal data, making secure evaluation practices essential. First, consider using secure cloud storage options that offer encryption both in transit and at rest. This reduces the risk of unauthorized access and data breaches.
Additionally, access to these storage solutions should be strictly controlled. Only authorized personnel should be granted permissions to view or edit the stored forms. Regular audits of these access controls help ensure that only the necessary individuals have the ability to handle sensitive evaluations. Implementing version control systems can further enhance your storage solutions by preserving previous iterations of the documents, allowing for streamlined corrections while maintaining data integrity. By focusing on proper storage strategies, organizations can foster trust and protect valuable employee information effectively.
Access Control and Authentication
Access control and authentication are vital components in maintaining the integrity of secure evaluation practices. Limiting access to employee evaluation forms ensures that only authorized personnel can view or edit sensitive information. This practice is crucial to guard against unauthorized access, which could lead to data breaches or misuse of sensitive employee data.
To enhance security, implementing multi-factor authentication (MFA) is essential. MFA adds an extra layer of protection by requiring multiple forms of verification before granting access. Furthermore, it is important to regularly update access permissions, ensuring that only current staff members have access to evaluation forms. By proactively managing who can view or modify these documents, organizations can mitigate risks and uphold data integrity. Such approaches not only safeguard sensitive information but also foster trust among employees and enhance overall efficiency in the evaluation process.
Limiting access to evaluation forms to authorized personnel mitigates unauthorized access risks.
Limiting access to evaluation forms to authorized personnel significantly reduces the risk of unauthorized access. This practice ensures that only trained staff who need access can view, edit, or manage sensitive evaluations. By restricting access, organizations create a more secure environment, minimizing the potential for data breaches or misuse of confidential information.
To further enhance security, implementing multi-factor authentication is essential. This adds an additional layer of protection, verifying identities before granting access to evaluation forms. Regularly updating access permissions ensures that former employees or individuals who no longer require access cannot retrieve sensitive data. By adopting these secure evaluation practices, call centers can mitigate unauthorized access risks effectively and foster a trustworthy evaluation process for all employees.
- Step 1: Implement Multi-Factor Authentication
Implementing Multi-Factor Authentication (MFA) is a critical step in enhancing the security of call center employee evaluation forms. MFA adds an extra layer of protection by requiring users to provide two or more verification factors to gain access. This significantly reduces the risk of unauthorized access, as a compromised password alone is not enough for entry.
There are several components to consider when implementing MFA. First, identify the right authentication methods for your organization. These may include hardware tokens, mobile authentication apps, or biometric verification. Next, ensure that all employees are trained to use MFA effectively. Continuous monitoring of access and authentication logs can help identify potential breaches early on. By adopting MFA, you reinforce secure evaluation practices and enhance overall data integrity, fostering a more secure environment for sensitive employee evaluations.
- Step 2: Regularly Update Access Permissions
Regularly updating access permissions is a fundamental aspect of maintaining secure evaluation practices in a call center environment. Each employee should only have access to the sensitive information necessary for their role. Over time, roles may change, and employees may transition out, making it crucial to regularly review and adjust access permissions accordingly. Employers should establish a routine, perhaps quarterly, to audit who has access to evaluation forms and ensure thatappropriate changes are made promptly.
Additionally, implementing a systematic process for granting and revoking access is vital for security. This includes documenting all access changes and keeping a log of who accesses the data and when. By doing so, organizations can better track compliance with security protocols. Regularly updating access permissions not only protects sensitive employee information but also reinforces trust among the workforce, ensuring that everyone understands the importance of secure evaluation practices in their daily operations.
💬 Ask About This Article
Have questions? Get instant answers about this article.
Extract insights from interviews, calls, surveys and reviews for insights in minutes
Tools for Secure Evaluation Practices
To ensure robust secure evaluation practices, utilizing the right tools is paramount. A variety of available software solutions can enhance the protection of evaluation forms while simplifying their management. The choice of tools can significantly influence data security levels and ease of use for employees involved in the evaluation process.
Some recommended tools for secure evaluation practices include SecureDocs, LockBox, SecureFormManager, and DataGuardPro. Each of these tools offers unique features that contribute to data encryption, user authentication, and integrated access control. For instance, SecureDocs provides comprehensive data protection and tailored encryption options, making it ideal for handling sensitive employee evaluations. Meanwhile, tools like LockBox and SecureFormManager focus on user-friendly interfaces that comply with security regulations, thereby maintaining the integrity of evaluation data. By leveraging these tools, organizations can ensure that their employee evaluations are safeguarded against unauthorized access and data breaches.
Explore top tools designed to enhance the security of call center employee evaluation forms.
To enhance the security of call center employee evaluation forms, leveraging specialized tools can be critical. Such tools help encrypt sensitive data and ensure only authorized personnel have access. Using advanced data protection methods can significantly reduce the risk of breaches, keeping both employee and organizational information safe.
Among the top tools available, SecureDocs stands out for its user-friendly interface and robust encryption features. LockBox excels in access management, ensuring only vetted staff view sensitive evaluations. SecureFormManager further enhances data integrity by automating secure storage protocols. Lastly, DataGuardPro offers customizable security solutions suitable for various operational needs. By integrating these tools into the evaluation process, call centers can adopt secure evaluation practices that bolster employee trust and data protection.
insight7
Implementing secure evaluation practices is essential for maintaining the confidentiality of sensitive employee information in call centers. Employees often share personal data during evaluations, making it vital to adopt best practices for safeguarding this information. Utilizing advanced encryption techniques is one effective way to protect data from unauthorized access, ensuring that the transmission and storage of evaluations remain confidential.
Another key element is access control. Limiting access to evaluation forms solely to authorized personnel significantly reduces the risk of data breaches. Multi-factor authentication serves as an additional layer of protection, verifying user identity before granting access. Regularly updating permissions further helps maintain a secure environment. Following these secure evaluation practices enhances the integrity of the evaluation process, ultimately building trust within the organization and ensuring compliance with data protection regulations.
insight7 offers advanced data protection and encryption features tailored for secure evaluation form management.
The implementation of advanced data protection and encryption features is essential for secure evaluation form management. These capabilities ensure that sensitive employee information is kept confidential and protected from unauthorized access. Organizations should prioritize encryption protocols that safeguard data both in transit and at rest. This proactive approach fosters a secure environment, mitigating risks associated with data breaches.
When selecting data protection tools, ensure they offer robust security features tailored to evaluation forms. This means integrating solutions that not only enhance encryption but also streamline the overall management of sensitive data. Employing advanced technology allows call centers to create secure evaluation practices that inspire trust among employees and stakeholders. By harnessing these features, organizations can effectively manage evaluation forms with peace of mind, knowing that employee data is thoroughly protected from potential threats.
Additional Tools
Expanding your toolkit for secure evaluation practices is vital for enhancing employee evaluation forms in call centers. Various additional tools can significantly enhance your capability to protect sensitive information. Among these, SecureDocs provides comprehensive document protection and user access management, essential for safeguarding evaluation data during transfer and storage.
Similarly, LockBox offers an intuitive interface for secure file-sharing, ensuring that only authorized personnel can access evaluation forms. SecureFormManager streamlines the process of collecting employee feedback while incorporating advanced security protocols. Finally, DataGuardPro integrates additional encryption measures, ensuring that all data remains confidential and secure. Utilizing these tools effectively will bolster secure evaluation practices, allowing call centers to protect sensitive information while promoting efficiency and compliance.
- Tool 1: SecureDocs
SecureDocs is an essential tool that supports secure evaluation practices for call center employee evaluation forms. With its user-friendly interface, SecureDocs allows staff members to easily access and manage sensitive documents without requiring extensive technical knowledge. This democratization of access helps streamline processes while preserving security.
One of the key features of SecureDocs is its advanced encryption, which safeguards sensitive data during transmission and storage. By employing robust encryption protocols, the tool ensures that only authorized personnel can access employee evaluation forms. Additionally, SecureDocs facilitates the implementation of access controls, such as multi-factor authentication, making it difficult for unauthorized users to compromise data security. Utilizing SecureDocs effectively can provide peace of mind to organizations, allowing them to focus on enhancing their evaluation processes while safeguarding their employees' sensitive information.
- Tool 2: LockBox
LockBox provides an innovative solution for enhancing secure evaluation practices in call centers. This tool creates a virtual environment where sensitive employee evaluation forms are stored securely. Users can easily upload, manage, and access documents, all while maintaining stringent security measures. LockBox utilizes encryption protocols that ensure data is protected both in transit and at rest, significantly reducing the risk of unauthorized access.
Moreover, LockBox allows for customizable access controls, ensuring only authorized personnel can view or edit sensitive content. By implementing multi-factor authentication, the tool adds an additional layer of security, making it difficult for unauthorized users to breach the system. Overall, the capabilities of LockBox not only safeguard employee evaluation forms but also promote a culture of security within the organization, making it an indispensable asset for any call center seeking to strengthen their secure evaluation practices.
- Tool 3: SecureFormManager
SecureFormManager is a vital tool designed specifically to uphold secure evaluation practices for call center employee evaluation forms. With its advanced features, SecureFormManager ensures that sensitive employee data is protected through robust encryption methods. This tool not only allows for secure data storage but also facilitates seamless transmission, significantly reducing the risk of data breaches.
Moreover, SecureFormManager incorporates strong access controls, ensuring that only authorized personnel can access the evaluation forms. This functionality includes features such as multi-factor authentication and regular access permission reviews. By implementing such measures, organizations can maintain confidentiality and trust while ensuring compliance with industry standards. Ultimately, SecureFormManager serves as an essential asset in cultivating a secure environment for employee evaluations, enhancing both security and efficiency within call center operations.
- Tool 4: DataGuardPro
DataGuardPro is a powerful tool designed to enhance secure evaluation practices for call centers. This platform prioritizes data protection, ensuring that sensitive employee evaluation forms are safeguarded against unauthorized access. With its user-friendly interface, it streamlines the evaluation process while maintaining high levels of security necessary in today’s data-driven environment.
Key features of DataGuardPro include end-to-end encryption, which protects data in transit and at rest. It also employs robust access control measures, allowing only authorized personnel to handle evaluation forms. Regular update protocols ensure that access rights reflect any changes in personnel or roles, mitigating potential security risks. By implementing DataGuardPro, call centers can streamline their evaluation processes without compromising the confidentiality and integrity of employee information. Adopting such sophisticated tools is vital for maintaining trust and elevating secure evaluation practices within any organization.
Conclusion: Strengthening Secure Evaluation Practices
Implementing secure evaluation practices is essential to maintaining the integrity of call center employee evaluations. By prioritizing data protection through encryption and controlled access, organizations can foster a safe environment for sensitive information. Employees can feel confident their evaluations are handled with care, thereby encouraging open dialogue and continuous improvement.
In addition, using specialized tools can streamline and strengthen these secure evaluation practices. Regular training on security policies and updates further enhances the reliability of evaluation processes. By committing to these measures, call centers not only comply with security standards but also build trust with their employees, ultimately leading to a more effective, engaged workforce.
In conclusion, adopting secure practices and utilizing the right tools are crucial steps in ensuring the security of call center employee evaluation forms. By following these guidelines, call centers can protect sensitive information and maintain trust.
To ensure the security of call center employee evaluation forms, adopting secure practices and utilizing the right tools are paramount. These steps not only help in safeguarding sensitive information but also contribute to maintaining organizational trust. By implementing strong encryption methods and access controls, call centers can significantly reduce the risks associated with data breaches.
Furthermore, regularly updating security measures and employing advanced tools will create a robust system for managing evaluation forms. Employees must feel confident that their information is handled securely, which in turn fosters a culture of transparency and accountability within the organization. Ultimately, embracing secure evaluation practices will fortify the integrity of the entire evaluation process.
Analyze & Evaluate Calls. At Scale.

💬 Ask About This Article
Have questions? Get instant answers about this article.