How to Ensure Secure Data Storage in Call Center Performance Reviews
-
Bella Williams
- 10 min read
In an age where data breaches frequently make headlines, the importance of Secure Review Storage in call center performance reviews cannot be overstated. Call centers accumulate vast amounts of sensitive data, which necessitates robust protection strategies. Ensuring the integrity and confidentiality of this information not only protects customers but also strengthens organizational trust.
Implementing Secure Review Storage involves understanding the unique data needs of call centers. Regular security audits, strong access controls, and encryption are essential measures that safeguard information. By prioritizing these strategies, organizations can create a secure environment that fosters compliance and bolsters performance review processes.
In todays digital age, maintaining the privacy and security of data is paramount, particularly in sensitive areas such as call center performance reviews. This blog post delves into the critical aspects of Secure Review Storage and provides actionable insights.
In today's digital age, maintaining data privacy and security is not just essential but a necessity, especially for sensitive areas like call center performance reviews. As organizations increasingly depend on data for performance assessment and employee development, the importance of Secure Review Storage cannot be overstated. Implementing secure methods ensures that sensitive information is kept confidential and compliant with regulations.
To effectively safeguard this data, it is crucial to incorporate robust security protocols. Start by evaluating current security measures to identify potential vulnerabilities. Next, establish strict access controls to limit who can view performance reviews, ensuring that only authorized personnel have access. Another key element is the use of data encryption, both for data in transit and at rest, which protects against unauthorized access. Lastly, conducting regular security audits is vital in maintaining the integrity of your storage and identifying areas for improvement. By following these steps, organizations can fortify their data security and enhance compliance with data protection regulations.
Analyze & Evaluate Calls. At Scale.
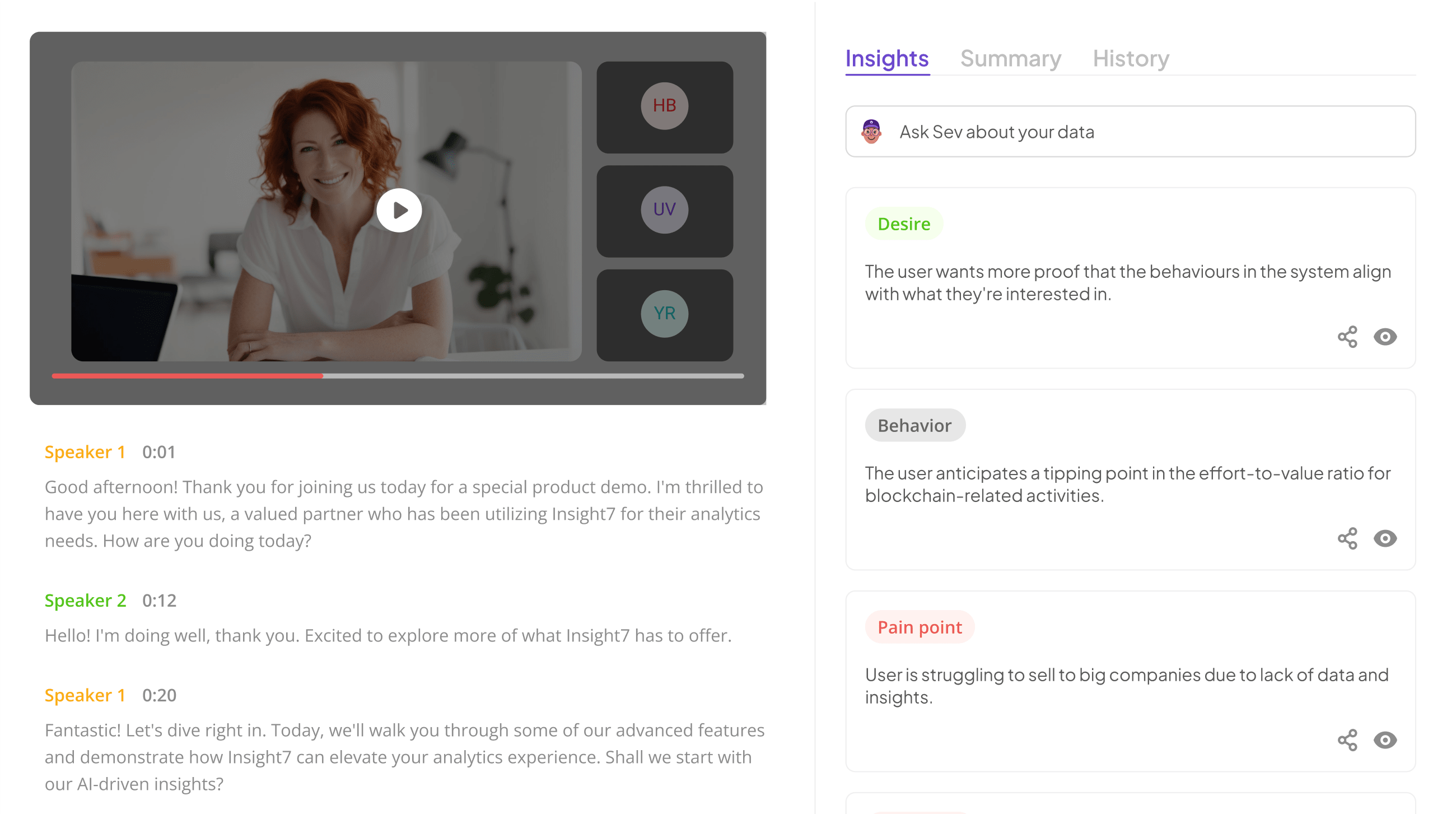
Importance of Secure Review Storage
Secure Review Storage is fundamental to maintaining the integrity and confidentiality of sensitive data in call centers. Implementing strong security measures ensures that performance reviews remain protected from unauthorized access. These reviews often contain personal and performance-related information that, if compromised, could lead to reputational damage and legal repercussions.
To achieve this, organizations must focus on several key areas. First, integrating robust access controls allows only authorized personnel to access sensitive review data. Second, employing encryption techniques for data both in transit and at rest can significantly enhance data security. Lastly, conducting regular security audits helps identify potential vulnerabilities and ensures compliance with relevant data protection regulations. By prioritizing Secure Review Storage, call centers can create a trustworthy environment where employee performance is assessed fairly and securely, thereby fostering a culture of accountability and growth.
Understanding the necessity of implementing robust security measures for performance reviews is crucial for compliance and confidentiality.
Implementing robust security measures for performance reviews is essential to safeguarding sensitive data. In the call center environment, performance reviews frequently include personal information that requires strict confidentiality and compliance with data protection laws. Establishing Secure Review Storage helps protect against unauthorized access, ensuring customer trust and regulatory compliance.
To achieve this, organizations should focus on several vital principles. First, they must implement strong access controls to guarantee that only authorized personnel can access performance data. Additionally, data encryption—both at rest and in transit—plays a crucial role in preventing data breaches. Regular security audits are also necessary to assess vulnerabilities and maintain the integrity of data storage systems. By prioritizing these strategies, organizations can secure their performance review processes, fostering an environment of accountability and respect for customer privacy.
Protecting Sensitive Information
To effectively protect sensitive information in call center performance reviews, implementing robust security measures is essential. Firstly, it is vital to recognize the types of sensitive data often included in these reviews, such as personal identification numbers and confidential client details. This understanding encourages a culture that values data confidentiality and ensures compliance with industry standards.
Secondly, several strategies can be employed to secure review storage effectively. Establishing strong access controls limits access to sensitive data, ensuring only authorized personnel can view pertinent information. Incorporating encryption both for data at rest and in transit is critical for safeguarding against unauthorized access during storage and transfer. Regular security audits further reinforce these measures, allowing for the identification and remediation of potential vulnerabilities in the system. By adopting these strategies, organizations can significantly enhance their Secure Review Storage practices, safeguarding sensitive information while maintaining transparency and trust with clients.
Call center performance reviews often contain sensitive information that requires protection from unauthorized access. This sub-section will explore methods to ensure data confidentiality.
Call center performance reviews often include sensitive information about customers and employees, which necessitates strong protection against unauthorized access. To ensure data confidentiality, organizations must implement a series of effective methods. Chief among these is the employment of robust access controls, which restrict access to only those personnel who require it for their roles. This helps to minimize data exposure and enhances security.
Another essential practice is data encryption. Encrypting sensitive information in storage and during transmission ensures that even if unauthorized access occurs, the data remains incomprehensible. Regular security audits play a vital role in maintaining overall data security, enabling organizations to identify and rectify any vulnerabilities in their protection measures effectively. By adopting these strategies, businesses can maintain Secure Review Storage that prioritizes the confidentiality and integrity of their performance reviews.
Compliance with Data Protection Regulations
Ensuring compliance with data protection regulations is essential for the secure storage of performance reviews in call centers. Organizations must adhere to regulations such as GDPR and HIPAA to protect sensitive information like personally identifiable information (PII). By implementing Secure Review Storage practices, companies not only fulfill legal obligations but also enhance customer trust.
To facilitate compliance, it is crucial to establish strong access controls, ensuring that only authorized personnel can view sensitive data. Additionally, encryption should be applied to data both at rest and in transit. Regular audits also play a significant role, allowing organizations to identify potential vulnerabilities and address them proactively. Overall, compliance with data protection regulations contributes to a safer data environment, ultimately leading to better call center performance and client satisfaction.
Review how Secure Review Storage aids in adhering to data protection regulations such as GDPR and HIPAA.
Secure Review Storage serves as a vital component in ensuring compliance with data protection regulations like GDPR and HIPAA. These regulations mandate strict guidelines regarding the handling and storage of sensitive information, particularly in industries that deal with personal data. By utilizing Secure Review Storage, organizations can implement robust encryption methods and access controls, safeguarding sensitive performance review data from unauthorized access or breaches.
Additionally, Secure Review Storage supports transparency in data handling practices. This transparency is crucial for demonstrating compliance and building trust with clients and stakeholders. Storing data securely not only mitigates risks but also ensures accountability, as organizations can track who accessed the data and when. Implementing this storage solution effectively helps to create a culture of responsibility regarding data privacy and security, ultimately fulfilling the requirements of regulatory frameworks.
Extract insights from interviews, calls, surveys and reviews for insights in minutes
Steps to Implement Secure Review Storage in Call Centers
To implement Secure Review Storage in call centers, organizations must follow a structured approach. Start by evaluating your current data security measures. This assessment helps identify vulnerabilities in existing protocols, ensuring that all potential weaknesses are addressed. It sets a solid foundation for strengthening security efforts.
Next, implement strong access controls. Establishing robust methods for authorizing personnel to access review data is crucial. It ensures that only selected team members can view sensitive information, significantly reducing the risk of unauthorized access. Following this, use encryption to protect data, both while it is stored and during transmission. Encryption enhances security by converting data into an unreadable format for unauthorized users.
Lastly, conduct regular security audits. These audits facilitate ongoing assessment of security practices, helping organizations detect potential lapses proactively. By consistently monitoring compliance with security protocols, call centers can maintain integrity and trust in their secure review storage practices. This layered security approach is essential for safeguarding sensitive performance review data.
A detailed guide on how to effectively secure data storage in call centers to protect performance reviews.
To effectively secure data storage in call centers for performance reviews, several key strategies must be employed. First, organizations should assess existing data security measures. Understanding current protocols helps identify weaknesses and areas needing improvement. By recognizing vulnerabilities, call centers can tailor their security strategies to protect sensitive performance review data more effectively.
Next, implementing strong access controls is essential. Limiting access to authorized personnel prevents unauthorized individuals from viewing performance evaluations. Additionally, employing encryption is crucial for data protection. Encrypting sensitive information both at rest and in transit ensures that even if data is intercepted, it remains unreadable. Regular security audits also play a vital role in maintaining secure review storage. These audits help identify potential lapses and strengthen overall security measures. By following these steps, call centers can achieve a robust system for secure review storage, ensuring that performance evaluations remain confidential and compliant with data protection regulations.
Step 1: Evaluate Your Current Data Security Measures
To ensure Secure Review Storage, begin by evaluating your current data security measures. This initial step is crucial for understanding what security protocols your call center currently has in place. Look for any gaps or vulnerabilities that may expose sensitive performance review data. Take the time to assess existing access controls, data encryption practices, and overall compliance with relevant regulations.
Next, analyze how well your security measures align with industry standards. Check if your data storage solutions are equipped to protect against potential threats, such as unauthorized access or data breaches. Ensuring that your security framework is robust not only safeguards sensitive information but also fosters trust among employees and stakeholders. A thorough evaluation sets a solid foundation for implementing stronger security measures, leading to improved compliance and enhanced data protection.
Begin by assessing the current security protocols in place to identify vulnerabilities.
To effectively ensure Secure Review Storage, it's essential to begin by assessing existing security protocols. This process involves a thorough examination of current practices that manage sensitive data within call center performance reviews. Identify any potential gaps or weaknesses that may lead to vulnerabilities, such as outdated software or insufficient access controls. Reviewing these protocols provides a foundation to understand where improvements can be made and sets the stage for subsequent steps.
Moreover, it’s crucial to categorize the types of data being handled. Look for areas where sensitive information, like social security numbers and birth dates, could be particularly at risk. Focusing on these aspects helps streamline efforts to reinforce security measures, safeguarding against unauthorized access. By prioritizing this assessment, you pave the way for effective strategies to protect data, ensuring that all performance reviews are securely stored and compliant with necessary regulations.
Step 2: Implement Strong Access Controls
Implementing strong access controls is essential for ensuring Secure Review Storage in call center performance reviews. To begin, establish a role-based access system that limits data access to only necessary personnel. This not only enhances data privacy but also reduces the risk of unauthorized disclosures. Training staff on access control policies further minimizes the chance of accidental breaches, keeping sensitive information secure.
Next, utilize multi-factor authentication (MFA) to add an extra security layer. This requires users to provide two or more verification factors to gain access, significantly reducing the risk of unauthorized access. Regularly review access permissions to ensure they remain aligned with personnel roles, adjusting as necessary when employees transition or depart. By following these procedures, you create a robust framework for maintaining the integrity of performance reviews while safeguarding confidential information.
Detail how to establish solid access control measures to ensure only authorized personnel can access review data.
To establish solid access control measures that ensure only authorized personnel can access review data, it is essential first to define user roles and permissions. By identifying the specific individuals or groups that require access, you can tailor permissions to restrict unnecessary access. This prevents sensitive performance review data from falling into the wrong hands, enhancing overall data security.
Next, implement a robust authentication process. Utilizing multi-factor authentication (MFA) adds an essential layer of security that requires multiple verification methods before granting access. This measure significantly lowers the risk of unauthorized access. Regularly updating and reviewing access permissions is also necessary, ensuring that only current employees retain access to review data. By following these steps, you can create a secure environment that protects sensitive information and preserves the integrity of performance review processes over time.
Step 3: Use Encryption for Data Protection
To effectively protect sensitive data within call center performance reviews, employing encryption is crucial. Encryption transforms data into an unreadable format, ensuring that even if unauthorized entities access it, they cannot decipher its contents. This provides a robust safety net for securing review data both at rest and in transit, enhancing the overall integrity of Secure Review Storage.
Implementing encryption involves a few key steps. First, ensure that all performance review data stored on your servers is encrypted using strong algorithms. Additionally, data transmitted between systems or users should also be encrypted to shield it from potential interception. Regular updates and reviewing encryption protocols will further bolster your data protection efforts, ensuring compliance with evolving regulations. By prioritizing encryption, you significantly bolster your call center’s data security measures and assure stakeholders of the integrity of their information.
Discuss the importance of encrypting sensitive data both at rest and in transit to enhance security.
Sensitive data, especially in call centers, must be secured at all times to prevent unauthorized access and breaches. Encrypting sensitive information both at rest and in transit enhances security significantly. When data is encrypted at rest, it is stored in a format that cannot be easily read by unauthorized personnel, ensuring confidentiality even if physical access is gained. In contrast, encrypting data in transit protects it while being transmitted, safeguarding it from interception by malicious actors.
This dual-layer approach is essential for achieving Secure Review Storage. By employing strong encryption methods, organizations can comply with stringent data protection regulations like GDPR and HIPAA, which require enforced security measures for personal data. Regularly updating encryption protocols and conducting security audits further strengthens these protections. As a result, call centers can maintain trust and confidentiality, fostering a secure environment for sensitive performance reviews.
Step 4: Conduct Regular Security Audits
Conducting regular security audits is essential for maintaining Secure Review Storage in call centers. These audits not only help identify potential vulnerabilities but also reinforce compliance with data protection regulations. Implementing a consistent schedule for security audits allows organizations to proactively uncover weaknesses in their data security measures and address them promptly.
During these audits, specific areas should be examined, including access controls, data encryption methods, and overall data management practices. By systematically reviewing these aspects, it becomes easier to identify discrepancies and implement necessary improvements. Regular security audits serve as a critical checkpoint to ensure that sensitive performance review data remains secure and is protected from unauthorized access, ultimately contributing to greater trust and accountability within the organization.
Explain the role of regular audits in maintaining Secure Review Storage and identifying potential security lapses.
Regular audits play a crucial role in maintaining Secure Review Storage by assessing compliance with security protocols and identifying potential vulnerabilities. These audits help organizations systematically evaluate the effectiveness of current security measures over time. By scheduling routine audits, businesses can ensure that any lapses in security are promptly addressed, minimizing the risk of unauthorized access to sensitive information.
Moreover, these audits create an opportunity for continuous improvement in security practices. During the audit process, organizations can pinpoint areas where their data handling processes may fail, such as outdated encryption methods or insufficient access controls. By proactively identifying these weaknesses, organizations not only enhance their Secure Review Storage but also fortify their overall data protection strategies. This diligent approach fosters a culture of security awareness within the team, leading to better practices and safeguarding valuable data against potential threats.
Top Tools for Ensuring Secure Review Storage
To ensure secure review storage in call centers, several tools stand out for their effectiveness and reliability. The first essential tool is data encryption software. This tool protects sensitive information by converting data into a secure format that only authorized users can read. Implementing encryption both at rest and in transit adds an extra layer of security against unauthorized access.
Next, consider access control management systems. These tools allow organizations to set permissions, ensuring that only authorized personnel can view and manage performance reviews. By establishing strong access controls, call centers can significantly reduce the risk of data breaches.
An additional useful tool is automated security auditing software. Regular audits help identify vulnerabilities in the data storage system and ensure compliance with security protocols. Lastly, compliance tracking tools provide insights into adherence to regulations like GDPR or HIPAA. By utilizing these tools, call centers can achieve and maintain secure review storage effectively.
Explore top tools that can aid in achieving secure data storage for call center performance reviews.
To achieve secure data storage for call center performance reviews, it is essential to explore the tools available that enhance security protocols. The right tools can help ensure that sensitive information remains protected while facilitating effective review processes. Various software solutions focus on providing robust security features tailored to analytics and data management needs.
Key tools to consider include advanced encryption software, which guarantees that data is unreadable to unauthorized users. Access control management systems are also vital, allowing organizations to restrict data access to authorized personnel only. Additionally, compliance tracking tools help monitor adherence to regulations such as GDPR and HIPAA, ensuring that your organization meets all legal obligations surrounding data storage. Regular audits and assessments are made easier with these tools, enabling continual evaluation of your data security measures. By investing in these technologies, call centers can create a secure review storage environment that upholds customer trust and compliance.
insight7
In ensuring Secure Review Storage, it's imperative to recognize the importance of robust data protection measures. The performance reviews conducted in call centers often involve sensitive information that could impact both employee privacy and company reputation if mishandled. By establishing strong security protocols, organizations can mitigate risks associated with data breaches and unauthorized access.
One critical step is the implementation of strong access controls. This means only authorized personnel should have access to performance reviews, minimizing the potential for data breaches. Additionally, using encryption for data both at rest and in transit is essential. Encrypting these reviews adds a layer of security, safeguarding sensitive information against interception. Regular security audits also play a vital role in maintaining the integrity of Secure Review Storage. These audits help identify any vulnerabilities that may have emerged over time and ensure that security measures remain effective as technology evolves.
Highlight how insight7 stands out as a premier tool for ensuring secure storage and efficient data management.
As organizations strive for excellence in call center performance, ensuring Secure Review Storage becomes indispensable. This is where insight7 excels as a premier tool, designed specifically for secure data management and efficient analysis. By providing an intuitive interface, it allows users to access sensitive data seamlessly, without requiring extensive training. This user-friendly design ensures that every team member can manage and analyze call data effectively while maintaining the highest standards of security.
The platform stands out with its robust data protection features that safeguard sensitive information through encryption and controlled access. Insight7 organizes all calls and transcripts in a secure library, enabling easy retrieval and analysis, essential for generating actionable insights. Furthermore, regular security audits and compliance tracking ensure that organizations uphold confidentiality and adhere to regulatory standards. By adopting insight7, call centers can confidently secure performance reviews, turning data management into a streamlined, efficient process.
Additional Tools
To enhance Secure Review Storage in call centers, it is essential to integrate a variety of additional tools specifically designed for data management. This not only ensures security but also streamlines the storage process. The right tools can significantly improve the way sensitive data, such as performance reviews, is handled.
One crucial tool is an advanced data encryption software, which safeguards stored information by transforming it into an unreadable format. Such a tool protects sensitive data from unauthorized access, making it indispensable for maintaining privacy. Another valuable option is access control management systems, which enforce strict permissions, ensuring that only authorized personnel can access particular data sets. Moreover, tools that facilitate regular security audits help identify vulnerabilities in the data storage systems, allowing quick remedial actions. Lastly, compliance tracking tools play a vital role in aligning with data protection regulations, helping organizations stay on top of legal requirements. By integrating these additional tools, call centers can significantly bolster their commitment to Secure Review Storage.
- Tool Name 1: Description on its suitability for data encryption.
Tool Name 1: Description on its suitability for data encryption.
In the quest for Secure Review Storage, Tool Name 1 emerges as a powerful solution for data encryption. By employing advanced encryption standards, this tool effectively safeguards sensitive information stored during call center performance reviews. Encryption transforms data into an unreadable format, ensuring that unauthorized users cannot access it, which is crucial for maintaining confidentiality in sensitive assessments.
Moreover, Tool Name 1 offers seamless integration with existing systems, allowing for secure data encryption both at rest and in transit. This feature is particularly important for call centers that process large volumes of performance review data, as it ensures that information remains protected across various platforms and storage locations. Regular security updates and compliance with industry regulations further enhance its reliability, making it an indispensable part of any strategy aimed at achieving Secure Review Storage.
- Tool Name 2: Overview of its access control management capabilities.
Tool Name 2 offers robust access control management capabilities essential for ensuring Secure Review Storage in call center performance reviews. This tool empowers organizations by allowing them to set permissions based on user roles. By implementing strict access restrictions, only authorized personnel can view sensitive performance review data, significantly reducing the risk of unauthorized access.
Additionally, the tool includes customizable access levels that align with the organization's compliance requirements. This means administrators can manage who sees what data based on specific roles, ensuring confidentiality. Collaboratively, these features promote an environment where data breaches are minimized, keeping sensitive information protected. Furthermore, auditing capabilities help track changes in access levels and identify any unauthorized attempts to access secure data. Hence, embracing these access control management features fosters a culture of security and accountability within the organization.
- Tool Name 3: Explanation of how it assists in conducting security audits.
Tool Name 3: Explanation of how it assists in conducting security audits.
The introduction of robust auditing tools is vital for maintaining Secure Review Storage in call center environments. These tools facilitate comprehensive evaluations of security protocols, ensuring that sensitive performance review data remains protected. By tracking access logs and identifying unauthorized attempts to view or modify data, this tool strengthens your security posture.
Regular audits play a significant role in the security framework. Utilizing this tool, organizations can proactively uncover vulnerabilities and adjust their security measures accordingly. This continuous feedback loop is crucial for compliance with data protection regulations, allowing for timely responses to potential threats. Ultimately, leveraging effective auditing solutions is essential for establishing and maintaining Secure Review Storage, ensuring that sensitive information within call center performance reviews is always safeguarded.
- Tool Name 4: Insights on its compliance tracking features.
Tool Name 4 offers robust compliance tracking features that significantly enhance the management of secure review storage. One of the key functionalities is its ability to create customizable evaluation templates tailored to different compliance standards. This ensures that every call center performance review aligns with required regulations, enabling teams to meet industry standards consistently.
Additionally, this tool allows for comprehensive tracking of compliance metrics throughout the review process. By analyzing calls against specified criteria, it ensures that every performance review reflects not only quality assurance but also adherence to data protection regulations. Regular compliance updates and audits can be incorporated, providing peace of mind regarding secure review storage and safeguarding sensitive information. Overall, the integration of robust compliance tracking makes Tool Name 4 a powerful asset in achieving effective and secure data management in call center environments.
Conclusion: Achieving Secure Review Storage for Call Center Performance Reviews
In conclusion, achieving secure review storage for call center performance reviews is essential to safeguarding sensitive data. By implementing measures such as strong access controls and encryption, organizations can effectively minimize the risk of unauthorized access. Regular security audits further enhance the integrity of the data storage process, ensuring that only authorized personnel handle sensitive information.
Moreover, leveraging advanced tools specifically designed for secure review storage streamlines the entire process while maintaining compliance with data protection regulations. By prioritizing security and adopting a proactive stance, call centers can protect valuable performance insights and build trust with their workforce.
Summarize the critical steps and tools discussed to ensure that call center performance reviews are stored securely, highlighting the importance of a proactive approach to data security.
To ensure that call center performance reviews are stored securely, it is crucial to adopt a proactive approach to data security. Start by assessing the current data security measures, identifying vulnerabilities that may expose sensitive information. Implement strong access controls to ensure only authorized personnel have access to crucial review data. Additionally, encrypt sensitive data at rest and during transit to protect it from unauthorized access.
Regular security audits are essential for maintaining secure review storage and identifying potential lapses in security protocols. Utilize reliable tools that specialize in data security measures. Consider software solutions that offer data encryption, access control management, and compliance tracking. By prioritizing these steps and tools, organizations can effectively safeguard performance review data, fostering an environment of trust and compliance. Secure Review Storage should not be an afterthought but an ingrained practice for optimizing data privacy policies in call centers.